
Introduction to Ransomware Attacks
Ransomware attacks are becoming more dangerous and can bring people and businesses to their knees. In simple words, ransomware is bad software that encrypts the data of the victim, making it impossible to access. The attacker then asks for a ransom in exchange for the decryption key, so the victim’s data is essentially held hostage. This bad strategy has become very popular among hackers because it is very profitable and easy to use.
How Ransomware Attacks Work
Infiltration and Encryption
Ransomware attacks typically commence with the cybercriminal infiltrating a target system through various means. These may include phishing emails, malicious attachments, or exploiting vulnerabilities in software. Once inside, the attacker deploys the ransomware payload, which rapidly encrypts files and data on the victim’s device. The encryption renders the data unreadable and practically useless.
Ransom Notes and Demands
When the attack is successful, the attacker leaves a ransom note with the terms and how to pay. Most of the time, victims are given a short amount of time to pay the ransom, which is usually in cryptocurrency like Bitcoin, in order to get the access key. The ransom amount is very different, and some people have asked for absurd amounts. Even if you pay the ransom, you may not be able to get your data back because the hackers may just disappear or give you a bad decryption key.
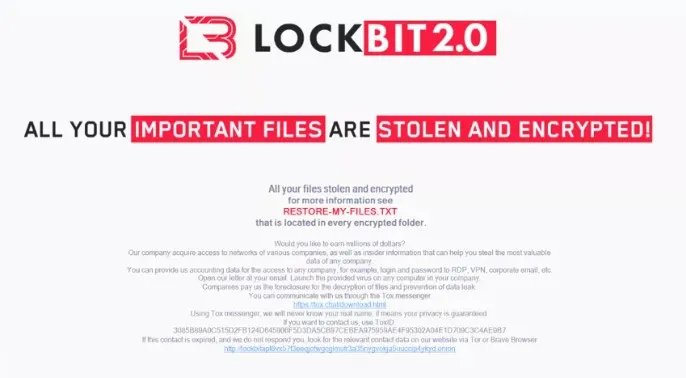
The Evolution of Ransomware
Traditional Ransomware
Early versions of ransomware were pretty simple. They targeted individual users and asked for small ransoms. Most of the time, these attacks were random and used mass-distributed emails with infected files. As cybersecurity defences got better, hackers changed how they did things, which led to ransomware that is more complicated.
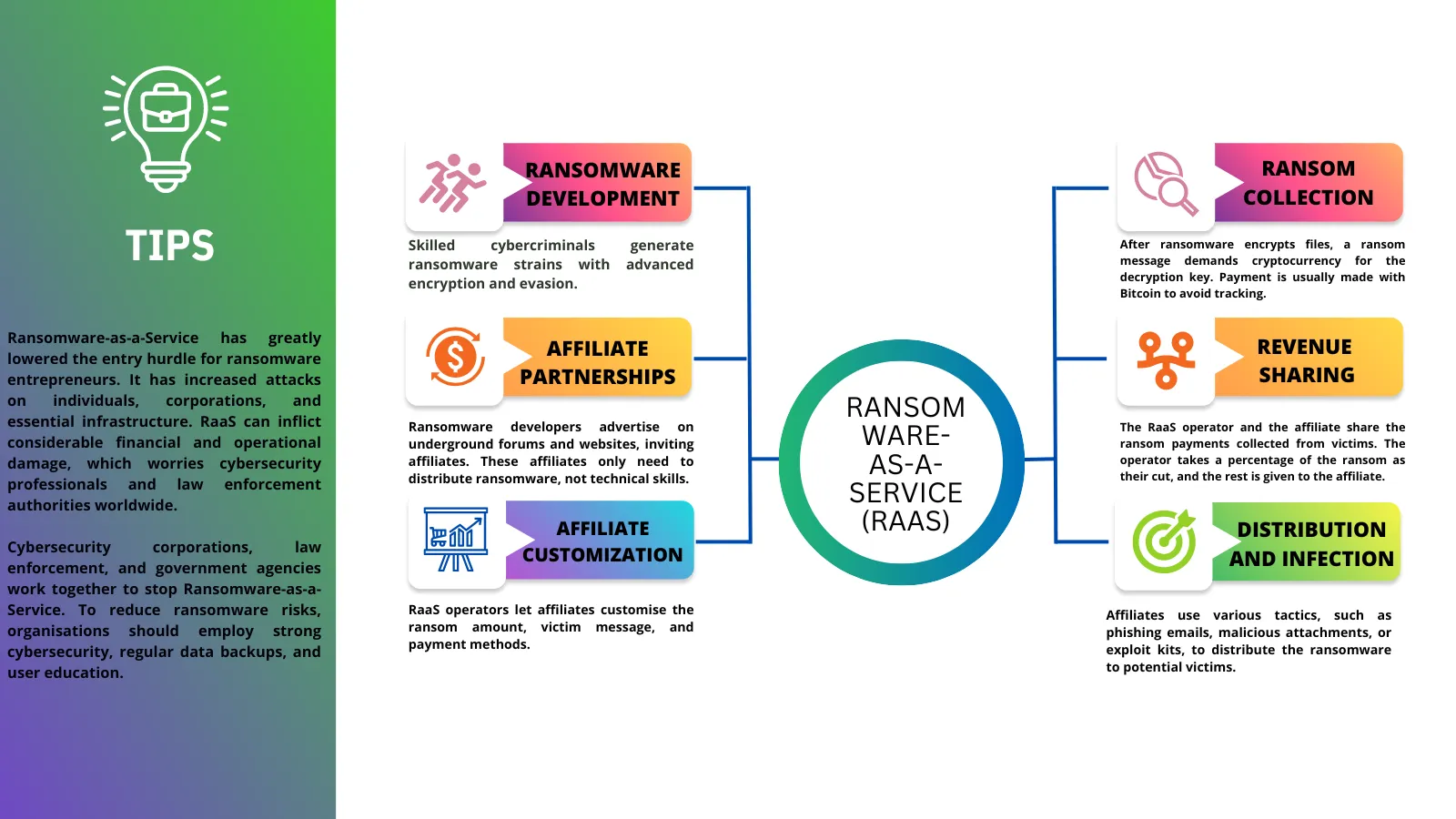
Ransomware-as-a-Service (RaaS)
ransomware-as-a-Service (RaaS) is a cybercriminal business model in which people who make or run ransomware rent out their ransomware software to other people or groups, often called “affiliates” or “partners,” who then use it to launch their own ransomware attacks. Even people with little technical knowledge can use this model to launch ransomware attacks because they can basically “rent” the ransomware infrastructure and tools from the people who made them.
Double Extortion Ransomware
Recent ransomware attacks have taken a more dangerous turn by using double blackmail. In addition to encrypting data, attackers also steal private information before deploying the encryption payload. With this dual-threat method, cybercriminals can use the threat of leaking confidential information if the victim doesn’t pay the ransom to get what they want. This evil plan makes it harder for victims not to give in to the attacker’s requests.
The Far-Reaching Consequences
Financial Losses
Ransomware attacks cause people to lose a lot of money. Organisations have to deal with more than just paying the ransom. They also have to deal with operating downtime, recovery costs, and possible legal liabilities. Small businesses may find it hard to get back on their feet after the financial hit, which could lead to their closing and the loss of jobs.
Reputational Damage
After a ransomware attack, an organization’s image is often hurt. When a customer hears about a hack, it can hurt their trust and confidence, which could make them leave. Restoring a bad image through public relations can take a lot of time and resources.
Legal and Regulatory Ramifications
Attacks by ransomware could lead to legal and regulatory problems. Depending on the type of data that was leaked and the laws in place, organizations may have to pay fines for not taking enough steps to protect data. Compliance problems can make the financial damage of an attack even worse.
Notable Ransomware Attacks in Recent Years
WannaCry: A Global Catastrophe
The WannaCry ransomware attack of 2017 sent shockwaves all over the world. WannaCry quickly spread across networks and encrypted files on a scale that had never been seen before. It did this by taking advantage of flaws in old Windows operating systems. Hospitals, government agencies, and businesses were all affected, which shows how important it is to update software and take other security steps quickly.
Colonial Pipeline: Fueling Panic
In 2021, the Colonial Pipeline ransomware attack showed how these kinds of breaches affect people in the real world. Because of the attack, a major fuel supply had to be shut down, which led to fuel shortages and panic buying across the eastern United States. This event showed how key infrastructure is vulnerable to ransomware threats.
Health Service Executive Ransomware Attack
On May 14, 2021, Ireland’s Health Service Executive (HSE) was hit by a big ransomware cyberattack that affected many people. The attack, which was caused by the Conti virus and led by a criminal group called Wizard Spider, shut down all HSE IT systems across the country.
The HSE ransomware attack had major effects on both medical services and data about patients In response to the attack, all of the HSE’s IT systems were shut down, which messed up key services and caused many appointments to be cancelled.
There was a lot of trouble with how the hospital ran, which messed up patient care and treatment plans.
There have been medical data breaches, where private patient information was stolen and put online
The HSE’s business papers were posted online, putting sensitive information at risk.
Ransomware Payment Dilemma: To Pay or Not to Pay?
Ethical and Legal Considerations
There are a lot of moral and legal problems with paying a ransom. Paying the ransom makes ransomware attacks more profitable, which encourages hackers to keep doing bad things. Also, giving money to criminal organisations may unintentionally help other types of cybercrime, which keeps the circle of harm going.
Impact on Future Attacks
Paying the ransom doesn’t ensure that your data will be restored or that you won’t be attacked again. Cybercriminals may take advantage of a victim’s weakness by attacking them again or sharing their information with other criminals. Before paying a debt, organisations should carefully think about what might happen.
Protecting Against Ransomware Attacks
Robust Backup and Recovery Strategies
It is very important to back up important data regularly and in a safe way. With clean and up-to-date backups, organisations can recover their systems and data in the event of a ransomware attack without having to pay the ransom. To keep backups from being hacked, they should be kept offline or in separate places.
Multi-Layered Security Measures
Multiple layers of defence are needed for a full cybersecurity plan. Attacks from ransomware can be stopped by using advanced security software, firewalls, intrusion detection systems, and email filters. To stay ahead of new risks, security needs to be checked and updated regularly.
Employee Training and Awareness
Human error remains a significant vulnerability in ransomware attacks. Cybercriminals often exploit employees through phishing emails or social engineering tactics. Educating staff about cybersecurity best practices, recognizing suspicious emails, and avoiding clicking on unknown links can fortify an organization’s defenses.
The Role of Cybersecurity Professionals
Incident Response and Recovery
When ransomware attacks happen, cybersecurity experts are a key part of the solution. Strategies for responding to incidents that are quick and work well can help stop the attack, limit the damage, and speed up healing. Digital forensics experts can look at attack vectors, figure out where the breach came from, and gather proof for possible legal action.
Collaborative Efforts to Combat Ransomware
Government and Law Enforcement Initiatives
The world’s governments and law enforcement agencies are working harder to stop ransomware strikes. International groups are working together to find and catch hackers, break up ransomware networks, and improve cybersecurity laws.
Private Sector Partnerships
The private sector is also working together to fight malware. Industry groups, cybersecurity firms, and tech companies work together to share information about threats, come up with ways to protect themselves, and spread best practises.
Emerging Trends and Future Outlook
AI-Powered Ransomware
The combination of artificial intelligence and ransomware is a threat that is getting closer and closer. AI-driven attacks could use machine learning algorithms to target weaknesses, change tactics, and figure out how much ransom to ask for. This would make them even more dangerous and hard to stop.
Targeting Critical Infrastructure
Ransomware attacks on important infrastructure, like power lines, water supply systems, and transportation networks, are very dangerous and could lead to disaster. Cybercriminals are going after vital services, so governments and organisations need to improve their cybersecurity defences to keep people safe.
Ransomware in the Internet of Things (IoT) Era
As Internet of Things (IoT) gadgets become more common, ransomware attacks can happen in new ways. Cybercriminals can get in through smart products and industrial sensors that are connected to the internet. For the IoT ecosystem to be safe, it needs strong security steps and careful monitoring.
Conclusion
Ransomware attacks have grown into a serious threat that can cause a lot of damage. As cybercriminals continue to improve their methods and find ways to take advantage of weaknesses, it’s hard to say enough about how important it is to take preventative security steps. People and organisations can navigate this dangerous digital landscape and protect their data, operations, and future by knowing how ransomware attacks work, making their defences stronger, and working together.
Frequently Asked Questions
1. Can I trust cybercriminals to provide the decryption key after paying the ransom? It’s risky to believe what hackers say they will do. Some people who pay the ransom get the decoding key, but others do not. Paying the ransom also encourages crime and may not ensure that the data will be recovered.
2. Are there any alternative methods to recover data without paying the ransom? Yes, keeping backups of your data that are up-to-date is a good way to get your data back after a ransomware attack without paying the fee. You can make sure you have a clean copy of your data to restore by backing it up regularly and saving the backups offline.
3. How can organizations foster a culture of cybersecurity awareness among employees? Organisations can give their workers regular cybersecurity training to teach them how to spot phishing attempts, not click on suspicious links, and act in the safest way possible online. Simulations of scams can also help people be more aware.
4. How do cybersecurity professionals contribute to incident response and recovery? Cybersecurity experts figure out how big the breach is, find the systems that have been hacked, stop the attack, and start to fix the systems and data that have been damaged. They also work with law teams to figure out what to do next, like telling the police about the attack.
5. How can the public and private sectors collaborate to combat ransomware? Collaboration means sharing information about dangers, coming up with best practises, and working together on projects to stop ransomware. Partnerships between the public and private sectors can improve cybersecurity efforts and make it easier to respond to threats as a group.


