
Zero-Day Target NATO Summit Microsoft disclosed today a zero-day security bug in multiple Windows and Office products exploited in the wild to gain remote code execution via malicious Office documents
In this article, we will discuss a critical security flaw that has recently been disclosed by Microsoft. This zero-day vulnerability, tracked as CVE-2023-36884, affects multiple Windows and Office products and is currently being actively exploited in the wild. We will delve into the technical details of the bug, its potential impact on affected systems, and the steps Microsoft is taking to address this issue.
Understanding the CVE-2023-36884 Vulnerability
The CVE-2023-36884 vulnerability represents a significant threat to the security of Windows and Office products. It allows unauthenticated attackers to achieve remote code execution by leveraging malicious Office documents. One of the most alarming aspects of this exploit is that it does not require any user interaction, making it even more dangerous.
“Microsoft is investigating reports of a series of remote code execution vulnerabilities impacting Windows and Office products. Microsoft is aware of targeted attacks that attempt to exploit these vulnerabilities by using specially-crafted Microsoft Office documents,” Redmond said
“An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim. However, an attacker would have to convince the victim to open the malicious file.”
While the flaw is not yet addressed, Microsoft says it will provide customers with patches via the monthly release process or an out-of-band security update.
Impact and Risks
If successfully exploited, the CVE-2023-36884 vulnerability can result in a complete compromise of confidentiality, availability, and integrity. Attackers can gain unauthorized access to sensitive data, manipulate files, and potentially execute arbitrary code on affected systems. The implications of such a compromise are severe, posing significant risks to individuals, organizations, and even national security.
Mitigation measures available
Microsoft assures customers that they are shielded from phishing attacks exploiting the bug until the availability of CVE-2023-36884 patches. This protection extends to users utilizing Defender for Office and those who have activated the Attack Surface Reduction Rule “Block all Office applications from creating child processes.”
Those not using these protections can add the following application names to the HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftInternet ExplorerMainFeatureControlFEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key as values of type REG_DWORD with data 1:
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- PowerPoint.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
It is important to consider that configuring the registry key to prevent exploitation attempts may have an impact on certain functionalities associated with the mentioned Microsoft Office applications.

Exploited in attacks targeting NATO Summit attendees
According to a separate blog post by Microsoft, recent attacks directed at organizations participating in the NATO Summit in Vilnius, Lithuania, specifically targeted and exploited the CVE-2023-36884 bug.
According to reports written by Ukraine’s Computer Emergency Response Team (CERT-UA) and researchers from BlackBerry’s intelligence team, the attackers used fake documents that looked like they were from the Ukrainian World Congress organisation. Malicious payloads like the MagicSpell loader and the RomCom backdoor were sent out with these documents.
As documented in reports published by Ukraine’s Computer Emergency Response Team (CERT-UA) and researchers with BlackBerry’s intelligence team, the attackers used malicious documents impersonating the Ukrainian World Congress organization to install malware payloads, including the MagicSpell loader and the RomCom backdoor.
“If successfully exploited, it allows an attacker to conduct a remote code execution (RCE)-based attack via the crafting of a malicious .docx or .rtf document designed to exploit the vulnerability,” BlackBerry security researchers said.
“This is achieved by leveraging the specially crafted document to execute a vulnerable version of MSDT, which in turn allows an attacker to pass a command to the utility for execution.”
“The actor’s latest campaign detected in June 2023 involved abuse of CVE-2023-36884 to deliver a backdoor with similarities to RomCom,” Microsoft also said on Tuesday.
RomCom’s links to ransomware
RomCom is a Russian-based cybercriminal group (also tracked as Storm-0978) known for engaging in ransomware and extortion attacks alongside campaigns focused on stealing credentials, likely aimed at supporting intelligence operations, according to Redmond.
The gang was previously linked to the Industrial Spy ransomware operation, which has since switched to Underground [VirusTotal].
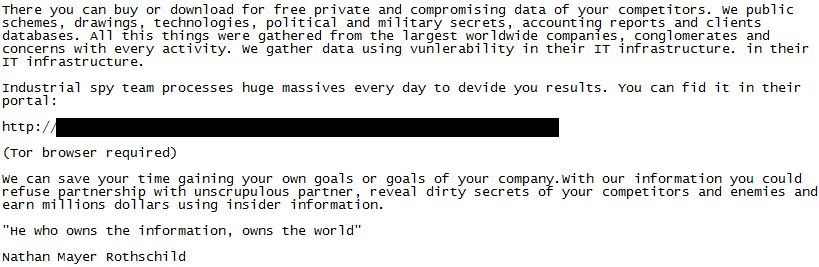
MalwareHunterTeam discovered a strange association with the Cuba ransomware operation in May 2022 while investigating the TOX ID and email address in an Industrial Spy ransom note.
e discovered that an Industrial Spy ransomware sample produced a ransom note with the same TOX ID and email address as Cuba, as well as links to Cuba’s data leak site.
However, instead of directing users to the Industrial Spy data leak site, the provided link led to Cuba Ransomware’s Tor site. Additionally, the ransom note used the same file name, !! READ ME !!.txt, just as previously identified Cuba ransom notes.


