The world of cybersecurity is a dynamic battleground in which law enforcement agencies use innovative strategies and technologies to tackle the ever-changing danger of bad actors. “Operation Duck Hunt,” a spectacular combined international effort led by the FBI and various European partners, is a recent colossal victory in this ongoing drama. The malevolent Qakbot botnet was successfully dismantled, dealing a severe blow to global criminality. Let us look into the complexities of this operation, the history of Qakbot, its evil activities, and the innovative strategy that resulted in its abolition.
Table of Contents
ToggleThe FBI’s Grand Disruption of Qakbot
Operation Duck Hunt was a joint effort between the FBI, Europol, and other law enforcement and justice agencies from around the world. This action was carefully planned to go after the Qakbot botnet, which had been causing trouble in the digital world for years. With a clever plan, law enforcement took down the Qakbot infrastructure and stopped its bad effects on devices that had been hacked.

Qakbot: A Malicious Evolution
Qakbot was first known as Qbot or Pinkslipbot. In 2008, it showed up as a banking worm. In the beginning, its main method of operation was to steal private financial information, like banking credentials and credit card numbers, in order to commit financial fraud. But as time went on, Qakbot’s skills grew, turning it into a platform for spreading different kinds of malware. Threat actors took advantage of Qakbot’s ability to gain initial entry to networks. This made it easier for them to launch ransomware attacks, steal data, and do other bad things online.
Ingenious Distribution Tactics
Qakbot is spread via a complicated game of lies, which is often done through clever phishing tactics. The “reply-chain” email attack is a notable method. In this attack, threat actors sneak into current email threads and hide their malicious payloads in attachments or links that look harmless. Attachments come in a lot of different forms, from Word and Excel files with harmful formulas to OneNote files with hidden content. Some even take advantage of holes in Windows that aren’t known to be there, which shows how flexible and adaptable malware is.
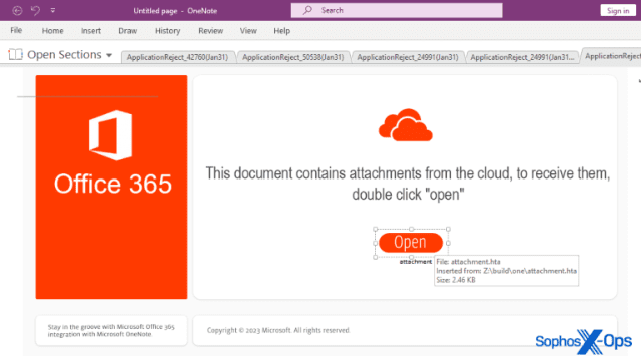
The Craft of Infection
Once Qakbot gets into a system, it uses a sneaky trick to hide itself in the memory of the system by blending in with legal Windows processes. This method, which includes putting malware into processes like wermgr.exe or AtBroker.exe, is designed to keep security software from finding it. Once the malware is running, it searches the system for valuable information to steal, such as email credentials that can be used in future phishing operations. Notably, Qakbot’s operators formed partnerships with other threat players, which gave them early access to their cybercriminal schemes, such as ransomware attacks.
Sinister Collaborations and Financial Gains
Throughout its illicit past, Qakbot has worked with well-known ransomware operations like Conti, ProLock, BlackCat/ALPHV, REvil, and others. From October 2021 to April 2023, the people who ran Qakbot got a whopping $58 million in cash payments. This huge amount shows how much money these cybercriminal organizations want to make.
Decoding Qakbot Operation Duck Hunt
In order to break up the Qakbot botnet, the FBI had to do a lot of different things. They had to carefully look at the layout of the botnet and plan how to get into its servers. An application for a seizure order revealed important information about the Qakbot operators’ admin computers, which helped figure out how the botnet worked. This structure was made up of Tier-1, Tier-2, and Tier-3 command and control servers. Each of these servers had a different job to do when it came to sending orders, updating malware, and sending malicious payloads.
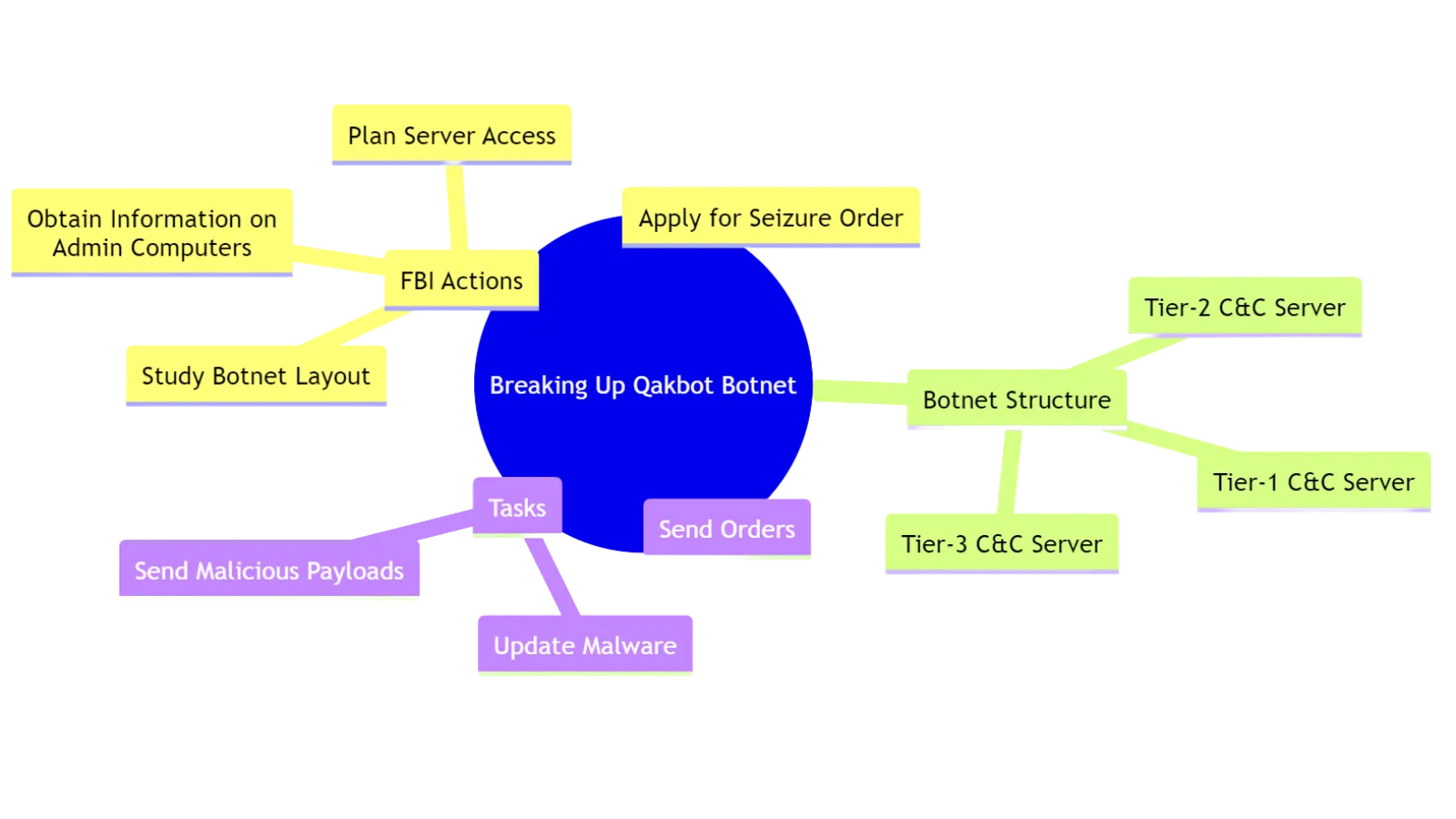
The Art of Disruption
The botnet’s command and control system was built around Tier-1 servers, which were infected machines that worked as “supernodes.” Surprisingly, some of these people were from the United States. Tier-2 computers, on the other hand, were run by the Qakbot operators themselves and were usually rented servers outside of U.S. jurisdiction. These middlemen sent encrypted messages to central Tier-3 servers, which were the brains of the botnet and made it easier for malware to spread.
The Critical Breakthrough
With encryption keys taken from infrastructure and devices that had been broken into, the FBI made a move that changed the game. They used a controlled device to connect to each Tier-1 server and replace the “supernode” module with one made by the police. This replacement used encryption keys that only the FBI knew, which stopped the Qakbot malware from talking to Tier-1 computers.
The Grand Finale
Following that compromised Tier-1 servers sent affected devices a special Windows DLL that could remove the malware. SecureWorks‘ analysis indicated that this custom DLL made Qakbot run the QPCMD_BOT_SHUTDOWN command, which shut down its processes. At 7:27 PM ET on August 25, the custom module was put into place, which stopped Qakbot from executing anything on compromised sites.
A Glimpse of the Future
The FBI stressed that the removal tool was approved by a court and could only be used to get rid of the malware, not to read or write to the hard drive. Even though we don’t know how many devices have been cleaned using this way, the FBI expects that more devices will be freed as they reconnect to the compromised Qakbot infrastructure.
Empowering Potential Victims
In an effort to help possible victims, the FBI gave services like Have I Been Pwned and the Dutch National Police access to a database of passwords stolen by Qakbot. This partnership makes sure that people can check to see if their credentials were stolen, which would mean they have been in contact with Qakbot’s bad impact in the past.
A Qakbot Operation Legacy of Success
Operation Duck Hunt wasn’t the first time the FBI has used a seizure order from the court to get rid of malware. In the past, successful operations have included stopping the Russian Snake malware from stealing data, taking apart the Emotet malware, and removing web shells from Microsoft Exchange servers when ProxyLogon attacks were happening. Even though there haven’t been any arrests, this is a win for law enforcement. However, the lack of arrests shows how Qakbot could come back through phishing efforts or by taking over other botnets.