
Introduction
In a striking revelation, the U.S. government has meticulously dissected the labyrinthine strategies employed by the Lapsus$ extortion group to infiltrate a multitude of organizations boasting robust security protocols. Their audacious methods, including the notorious SIM swapping technique, have left a trail of breaches that sent shockwaves throughout the cybersecurity landscape. Delving into this saga that unfolded over the course of 2021 and 2022, we unveil the intricate dance of Lapsus$, an enigmatic conglomerate largely composed of teenagers from the United Kingdom and Brazil. In this exposé, we’ll dissect their playbook, the alliances they forged, and the astonishing success that prompted them to be the cynosure of notoriety, wealth, and mischief.
The Lapsus$ Phenomenon
Lapsus$ emerged onto the scene with a loud bravado that was heard all over the digital world. This loosely-knit group got big companies like Microsoft, Cisco, Okta, and Nvidia caught in its web. Yet, the list looks like a who’s who of tech empires: T-Mobile, Samsung, Uber, Vodafone, Ubisoft, and Globant, all of which are subject to Lapsus$’s ravenous hunger for power. They were mostly teenagers from the U.K. and Brazil, and they wanted to make a name for themselves in the past of hacking, whether it was for money or just for fun.
SIM Swapping: The Art of Intrusion
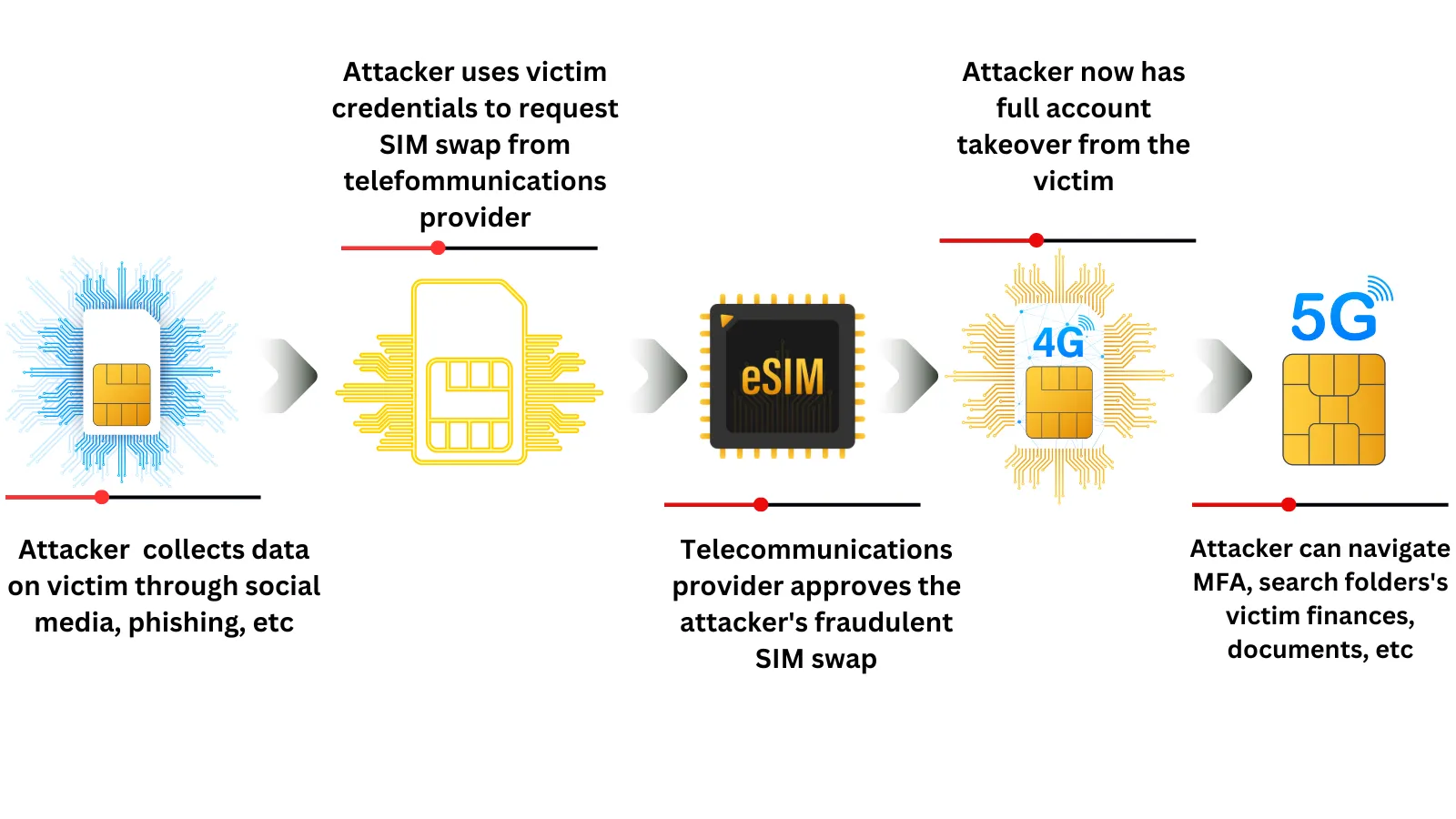
The SIM-swapping method is at the heart of their evil magic. It is a sneaky performance that involves stealing a victim’s phone number by transferring it to an attacker’s SIM card. This bold move depends on either social engineering or the help of someone who works for the victim’s cell phone company. Armed with the victim’s phone number, the attacker can intercept SMS-based codes that are used for two-factor authentication (2FA) into business systems or corporate networks.
How to solve the puzzle
When you look at how Lapsus$ runs his business, a troubling truth comes out. Fraudulent SIM changes were often set up by the group’s cleverly evil minds and came straight from the customer management tools of phone companies. By taking over the accounts of workers and contractors who didn’t know what was going on, this sneaky plan gave them a way to get into these digital strongholds. In order to get private information, they made up fake emergency disclosure requests (EDRs) in which they pretended to be real people or put government logos on the requests. This became their main method of operation.
Exploiting Weak Links
Lapsus$ demonstrated a persistent determination to infiltrate the innermost domains of their targets, displaying a proclivity for exploiting individuals with insider access within the organizations they aimed to breach. The individuals employed by the organization, as well as the contractors, unintentionally disclosed their login passwords, approved requests for multi-factor authentication (MFA), or allowed the group to get entry to domains that were otherwise limited in access. Equipped with a malevolent set of tools, Lapsus$ adeptly infiltrated the digital realm, deftly navigating through processes such as sign-in and account recovery with disconcerting proficiency.
Managing Business Risks
The Department of Homeland Security’s Cyber Safety Review Board (CSRB) uncovered Lapsus$’ dance with vulnerabilities that dot the digital landscape. Their dalliance with unpatched vulnerabilities in Microsoft Active Directory provided them with elevated privileges, a key to uncharted territories within the victim network. Astonishingly, the group’s proficiency with Active Directory vulnerabilities accounted for an astounding 60% of their exploits.
Adapting to Business Ups and Downs
In their inexorable march, Lapsus$ wielded a potent blend of effectiveness, speed, and audacity. Yet, their endeavours were not without their share of failures. Environments fortified by application or token-based multi-factor authentication (MFA) repelled their advances. The vigilance of robust network intrusion detection systems and the swift flagging of suspicious account activities thwarted Lapsus$’ machinations. Furthermore, organizations that adhered to incident response procedures witnessed mitigation of the impact.
Effective Risk Analysis Strategies
With the dust settled, the CSRB offers a trove of recommendations, an arsenal to fortify organizations against similar onslaughts. A shift to a passwordless environment fortified by secure identity and access management solutions is hailed as paramount. A categorical rejection of SMS as a two-step authentication method beckons. Strengthening authentication prowess to repel multi-factor authentication (MFA) phishing is advocated, as is the elevation of SIM swaps to the echelons of highly privileged actions, replete with stringent identity verification protocols. The clarion call for bolstered oversight and enforcement activities from the Federal Communications Commission (FCC) and Federal Trade Commission (FTC) resounds. A clarion call for a zero-trust model is in the air, along with a clarion order to build resilience against social engineering attacks.
The Silent Echoes
Since September 2022, Lapsus$ has been very quiet. This may be because key members were caught in the dragnet of police investigations that led to their arrest. The history of hacking will always remember this story. In March of the year before, seven people with ties to Lapsus$ were arrested by the City of London Police. Soon after, on April 1, two more teens, ages 16 and 17, were added to the list. In October, during “Operation Dark Cloud,” the Brazilian Federal Police caught a suspect with ties to Lapsus$. This person was behind a daring break-in at the Brazilian Ministry of Health..
Conclusion
The adventures of Lapsus$ are revealed to be a cautionary tale, crafting a tapestry that reverberates with audacity, mystery, and inventiveness. The legacy of Lapsus$ serves as a stark reminder that the guardians of cyberspace must adapt, innovate, and work together to fortify their defences lest they fall victim to the covert plots of those who dare to defy the boundaries of the virtual realm. As the digital world confronts an evolving threat landscape. The Lapsus$ case is similar to some of the groups we’ve studied previously.
Found this article interesting? Follow us on LinkedIn


