
A team of academics from the University of Wisconsin-Madison has shone a light on a serious issue in the field of cybersecurity. They’ve released a proof-of-concept Chrome Vulnerability extension that can harvest plaintext passwords directly from a website’s source code, which is now available in the Chrome Web Store. This study has shown a gap in the internet security armor, showing a systemic issue that should alert both website owners and users.
The Inadequate Permission Model
When you look more closely at the text input areas in web browsers, it’s clear that the permission model that Chrome uses to support extensions hasn’t lived up to expectations. This coarse-grained model doesn’t follow the rules of least privilege and full mediation. This leaves websites open to possible security breaches.
Placing Blame on Unrestricted Access
Researchers found that many high-traffic websites, including some run by tech giants like Google and Cloudflare, store their passwords in plaintext in their HTML source code. This made the situation even worse. This way of doing things makes it easy for extensions to get this private information.
The Heart of the Issue
The problem comes from the fact that Chrome browser plugins are often given full access to the Document Object Model (DOM) tree of a site. This gives them access to things like user input fields that could be private. Since there is no protection barrier between the extension and the site’s elements, the extension can access and extract any data from the source code.
Exploiting the Chrome Vulnerability
Worse, the app may directly access input data as users enter them in using the DOM API. This circumvents any attempt by the website to conceal private information. In essence, this means that the extension can steal data automatically.
The Manifest V3 Protocol
Even though Google Chrome made the Manifest V3 protocol to help with these problems, its main goal is to stop API misuse and stop people from using eval statements to run arbitrary code. It’s too bad that it doesn’t create a safe barrier between extensions and web pages, leaving content scripts open to attack.
A Test of Google’s Web Store Review Process
To test how well Google’s Web Store review process works, the hackers made a Chrome extension that could be used to steal passwords. This extension pretended to be a harmless GPT-based helper, which made it hard for static detection systems to spot it as dangerous.
Slipping Past Security Checks
The app was added to the Google Chrome Web Store after the review went well. The fact that the possible threat wasn’t found shows that the security checks weren’t very good. The researchers followed ethical rules and made sure that no real data was collected or used in the wrong way. Once the extension was accepted, it was taken off the shop right away.
Chrome Vulnerability to Attacks
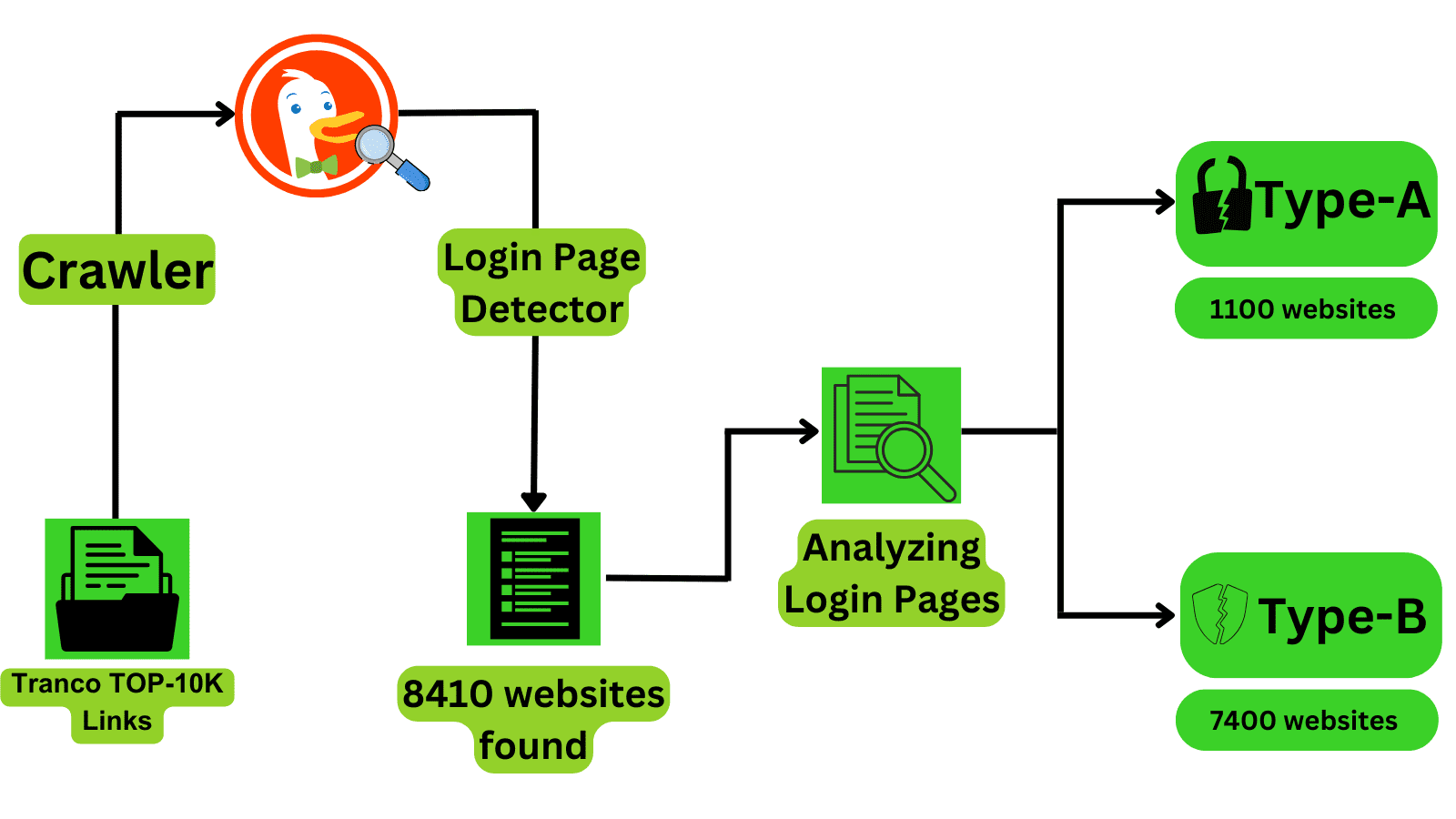
Also, a huge number of these websites (7,300) are open to DOM API access, which lets user input values be taken directly. This flaw makes it possible for bad people to get access to private user information without permission.
Methodology
The method used to find these shocking numbers is both complicated and telling. Researchers used a Chromium browser that was controlled by the Python Selenium library to take these measures. As described in their paper, they also added an extension that was made to carry out the attack.
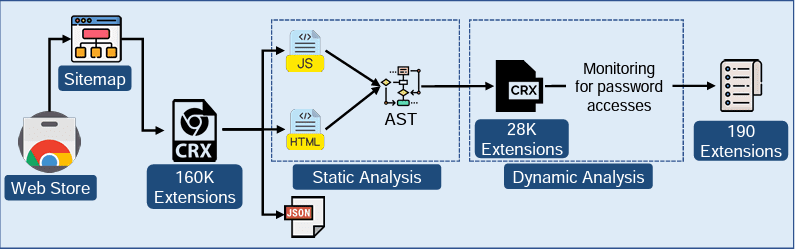
A Disturbing Statistic
Researchers from the University of Wisconsin-Madison wrote a technical study that says about 12.5% of Chrome Web Store extensions have the permissions they need to get sensitive information from websites. Some of them, like ad blockers and buying apps, have been downloaded millions of times.
A Potential for Exploitation
The research also shows that 190 extensions, some of which have been downloaded more than 100,000 times, access password fields directly and store the values they get. This makes people worried about how this security hole could be used.
Alarming Examples
The study says that there aren’t enough precautions on the following websites:
- gmail.com – plaintext passwords on HTML source code
- cloudflare.com – plaintext passwords on HTML source code
- facebook.com – user inputs can be extracted via the DOM API
- citibank.com – User inputs can be extracted via the DOM API
- irs.gov – SSNs are visible in plaintext form on the web page source code
- capitalone.com – SSNs are visible in plaintext form on the web page source code
- usenix.org – SSNs are visible in plaintext form on the web page source code
- amazon.com – credit card details (including security code) and ZIP code are visible in plaintext form on the page’s source code
List available here: tranco-list
Conclusion
In the end, this study shows how important it is to have better security measures for browser extensions and website protection. As users, we need to be aware of how our data is protected and hold developers and website owners accountable for keeping our private information safe.


