Mandiant Findings ShinyHunters Voice Phishing: SaaS Extortion Research

Executive Summary
Since June 2025, ShinyHunters cybercrime collective back to the life as a sophisticated voice phishing and SaaS extortion syndicate, according to Mandiant intelligence published January 2026. Operating under multiple threat cluster designations (UNC6661, UNC6671, UNC6240), the group has abandoned traditional database exploitation for a more insidious attack vector: impersonating IT support staff via telephone to capture SSO credentials, bypass multi-factor authentication (MFA), and pivot into cloud environments for bulk data exfiltration. Over six years, ShinyHunters has compromised 1+ billion user records across hundreds of organizations, evolving from opportunistic data thieves into a financially motivated extortion enterprise with reported coordination from Scattered Spider. Organizations with internet-facing identity platforms (Okta, Entra ID, Google Workspace) and SaaS-dependent workflows face immediate, high-severity risk in 2026.
Following a 12-month operational pause after four member arrests in June 2024, the group's January 2026 resurgence signals a fundamental tactical evolution from exploiting software vulnerabilities to weaponizing human trust. Mandiant confirms active exploitation continues across government, aviation, retail, and technology sectors globally, with the group demonstrating advanced social engineering capabilities that defeat traditional security controls.
The Flaw: Human Identity Verification Weakness
ShinyHunters' 2026 campaign exploits a critical-severity social engineering vulnerability in enterprise identity management workflows rather than software flaws. The attack chain leverages organizational weaknesses in help desk verification procedures and MFA enrollment processes to achieve unauthorized access to SaaS platforms containing sensitive customer, financial, and operational data.
Unlike traditional CVE-tracked vulnerabilities, this threat exploits procedural gaps where IT support staff verify caller identity using information already exposed in previous data breaches (employee ID numbers, Social Security numbers, manager names). The attack's effectiveness stems from the fundamental disconnect between identity verification rigor and the access privileges granted upon successful verification.
How the Exploit Works
ShinyHunters employs a five-stage attack methodology that combines voice phishing, credential harvesting, MFA manipulation, SaaS pivoting, and data exfiltration:
-
Voice Phishing (Vishing) - Initial Contact: Attackers call employees impersonating IT support, security teams, or third-party vendors. They leverage stolen PII from previous breaches (employee ID, SSN, manager name, internal project names) to establish credibility. Calls typically occur during off-business hours (2 AM - 4 AM local time) to reduce likelihood of verification with actual IT staff. The attacker creates urgency around password resets, MFA configuration updates, or security incident response requirements.
-
Credential Harvesting - Phishing Site Redirection: Victims are directed to sophisticated credential harvesting sites using brand-lookalike domains (e.g.,
yourcompany-okta[.]com,mycompany-sso[.]com). These sites capture SSO credentials in real-time while displaying legitimate-looking login interfaces that mirror the organization's actual identity provider. -
MFA Bypass - Help Desk Manipulation: Attackers call the organization's help desk impersonating the compromised user, using stolen PII to "prove" identity. They request enrollment of a new MFA device, claiming their primary device was lost or stolen. Help desk staff, lacking rigorous out-of-band verification procedures, enroll the attacker's device in the MFA system (Okta, Entra ID, Google Authenticator). Alternative method: attackers exploit session forgery techniques or deserialization vulnerabilities in identity provider workflows.
-
SaaS Platform Pivot - Lateral Movement: With valid credentials and enrolled MFA device, attackers authenticate to the organization's SSO portal and access downstream SaaS applications: Google Workspace (Gmail, Drive, Calendar, Contacts), Salesforce (CRM data, customer records, OAuth tokens), Microsoft 365 (SharePoint, OneDrive, Exchange, Teams), Atlassian (Jira, Confluence, source repositories), and DocuSign (signed contracts, audit trails).
-
Data Exfiltration - Bulk Export: Attackers use platform-native tools to extract data at scale: Google Takeout for bulk Gmail/Drive exports (500MB+ archives), Salesforce Data Loader for CRM record extraction via bulk API, PowerShell scripts for SharePoint/OneDrive downloads, and OAuth app authorization for persistent mailbox delegation. They delete security notification emails using Gmail's delete functionality to evade detection, operate outside business hours to avoid triggering anomaly alerts, and finally contact victims with extortion demands threatening data publication, regulatory reporting, or dark web sales.
Technical Example - Google Takeout Exfiltration:
# Attacker initiates Google Takeout export via compromised session
# Export targets: Gmail (all messages), Drive (all files), Contacts
# Archive size: 1.2 TB compressed
# Download initiated at 03:47 AM (outside business hours)
# User-agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
# Source IP: 185.220.101.XX (TOR exit node)
Detection Indicator:
Event: google.workspace.admin.TakeoutExportCreated
User: [email protected]
Archive Size: 1,247,893,442 bytes
Timestamp: 2026-01-28T03:47:22Z
Source IP: 185.220.101.XX (AS:tor-project)
Risk Score: CRITICAL
The "patch"—enhanced identity verification procedures, phishing-resistant MFA (FIDO2/passkeys), and help desk hardening protocols—remains inconsistently deployed across organizations. However, organizational awareness gaps and resistance to workflow changes have allowed exploitation to continue throughout January 2026 despite public threat intelligence warnings.
Timeline: From Zero-Day to Global Exploitation
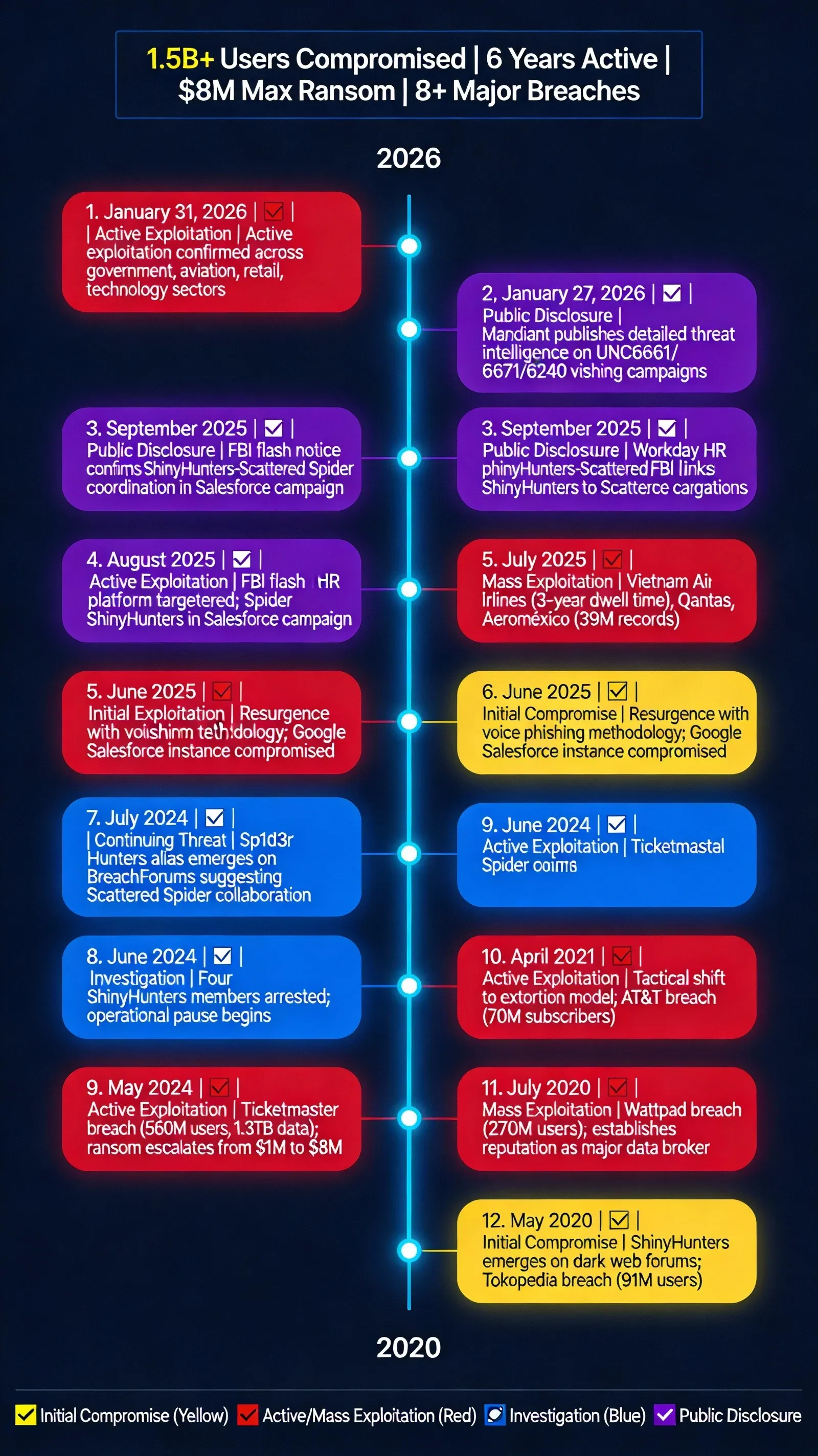
Who is Exploiting This? Threat Actor Attribution
ShinyHunters Primary Operations
ShinyHunters (tracked as UNC6040, UNC6240, UNC6661, UNC6671 by Mandiant) represents a decentralized cybercrime collective operating under a franchise model rather than a unified organization. The group name functions as a brand commanding premium pricing on dark web marketplaces.
- Targeting: Airlines, hospitality, retail, financial services, technology companies, SaaS providers, education software platforms
- Payload: Credential harvesting infrastructure, voice phishing scripts, OAuth token abuse, legitimate cloud exfiltration tools (Google Takeout, Salesforce Data Loader, PowerShell)
- TTPs: Voice phishing (vishing), help desk social engineering, MFA device enrollment manipulation, session token forgery, bulk data exfiltration, deletion of security logs, extortion via dark web leak sites ("Trinity of Chaos")
- Status: Active from May 2020 through January 2026; brief operational pause June 2024 - June 2025 following arrests; resurgence confirmed January 2026
Scattered Spider Collaboration
Scattered Spider (tracked as UNC6395, also known as Scattered Spider, Muddled Libra, 0ktapus) is a financially motivated threat actor group historically focused on retail supply chain intrusions and sophisticated social engineering attacks.
- Targeting: Retail trade, insurance, telecommunications, technology services
- Payload: Similar vishing infrastructure, MFA bypass tools, cloud access trojans
- TTPs: Voice phishing, SMS phishing, help desk manipulation, VPN abuse (Mullvad VPN), proxy networks for attribution masking
- Status: Active coordination with ShinyHunters confirmed August-September 2025; FBI flash notice validates operational alliance
Collaboration Evidence:
- Overlapping attack timelines targeting identical sectors (aviation July 2025, insurance June-August 2025)
- Shared infrastructure (Mullvad VPN, TOR exit nodes, brand-lookalike credential harvesting domains)
- Division of labor model: Scattered Spider provides initial access expertise; ShinyHunters provides exfiltration and monetization infrastructure
- "Sp1d3rHunters" alias emergence July 2024 suggesting brand merger or partnership framework
Financially Motivated Exploitation
| Actor | Geography | Primary Tools | Target Focus | Known Breaches |
|---|---|---|---|---|
| ShinyHunters (UNC6240) | Global operations | Voice phishing, Google Takeout, Salesforce Data Loader | Airlines, hospitality, SaaS providers | Ticketmaster, AT&T, Aeroméxico, Vietnam Airlines |
| Scattered Spider (UNC6395) | North America, Europe | Vishing, SMS phishing, proxy networks | Retail, insurance, telecommunications | MGM Resorts, Caesars Entertainment |
| UNC6661 | Unknown | MFA bypass, OAuth abuse | Technology, enterprise SaaS | Google (Salesforce), Cisco, Workday |
| UNC6671 | Unknown | Credential harvesting, session forgery | Financial services, healthcare | Under investigation |
The Commoditization of Enterprise Identity Theft:
ShinyHunters' evolution from database exploitation (2020-2021) to extortion-based operations (2021-2026) reflects a fundamental market optimization toward maximum revenue extraction. The group discovered that threatening regulatory reporting (GDPR violations, breach notification requirements) and data publication generates significantly higher returns than dark web data sales.
Example Revenue Comparison:
- 2020 Model (Data Sales): Tokopedia 91M records sold for ~$5,000 on dark web forums
- 2024 Model (Extortion): Ticketmaster 560M records, initial $1M ransom accepted, later escalated to $8M demand upon recognizing data value
- 2026 Model (SaaS Extortion): Google Salesforce instance breach, data threatened to be published via "Trinity of Chaos" leak site unless ransom paid (amount undisclosed)
This shift has lowered barriers to entry for financially motivated threat actors, as voice phishing requires no exploit development or vulnerability research—only social engineering skills and credential harvesting infrastructure readily available on criminal marketplaces.
Why This Matters: The Enterprise Identity Crisis
Key Challenges
-
Identity is the New Perimeter: Organizations have transitioned to cloud-first, SaaS-dependent architectures where identity platforms (Okta, Entra ID, Google Workspace) function as the primary security boundary. A single compromised identity with SSO access grants attackers lateral movement into every connected SaaS application—CRM systems, email, file storage, source code repositories, HR platforms, and contract management systems. ShinyHunters' targeting of identity providers rather than individual applications represents a force multiplier where one successful vishing call unlocks access to dozens of critical business systems.
-
MFA is Not Enough: Traditional MFA implementations using SMS codes, email verification, or push notifications remain fundamentally vulnerable to social engineering. ShinyHunters' help desk manipulation tactic—where attackers enroll new MFA devices by impersonating legitimate users—demonstrates that MFA provides a false sense of security when the enrollment process itself lacks rigorous verification. Organizations falsely believe MFA deployment equals comprehensive protection, while attackers systematically exploit the human-verification gaps in MFA lifecycle management.
-
Help Desk as Attack Vector: Enterprise help desk teams operate under pressure to resolve user access issues quickly, creating an inherent tension between security rigor and customer service metrics. Help desk staff typically verify caller identity using information readily available from previous breaches (employee ID numbers, manager names, Social Security numbers, internal project details). ShinyHunters weaponizes this verification weakness by conducting reconnaissance via previous data breaches (their own historical compromises provide the PII needed for current attacks), creating a self-reinforcing cycle where yesterday's breach enables tomorrow's compromise.
-
SaaS Logging Blind Spots: Many organizations lack comprehensive visibility into SaaS platform activity, particularly identity lifecycle events (MFA enrollment, OAuth token issuance, session token creation), bulk export operations (Google Takeout, Salesforce Data Loader), and after-hours access patterns. Without centralized logging of identity provider events and downstream SaaS activity, ShinyHunters operates undetected for extended periods—the Vietnam Airlines breach involved a 3-year dwell time before discovery.
-
The Franchise Threat Model: ShinyHunters operates as a decentralized brand rather than a unified organization, enabling resilience against law enforcement disruption. The June 2024 arrest of four members failed to dismantle the collective because new operators simply continued using the ShinyHunters brand. This franchise model creates attribution challenges (multiple UNC designations) and ensures operational continuity regardless of individual member arrests.
Defensive Posture: Immediate Actions
🔴 Emergency Session Revocation (Critical Priority - Execute Within 24 Hours)
- Revoke ALL active SSO sessions: Force re-authentication across Okta, Entra ID, Google Workspace, and all connected SaaS applications
- Terminate OAuth tokens: Revoke all authorized applications and service account tokens; require re-authorization with admin approval
- Reset privileged account passwords: Force password reset for all administrator, service desk, and privileged user accounts
- Disable self-service password reset: Temporarily disable self-service password reset portals; require manager approval + out-of-band verification for all password changes
- Lock MFA enrollment: Disable user ability to self-enroll new MFA devices; transition to admin-only MFA enrollment with mandatory identity verification
🔍 Detection & Response
Organizations must implement comprehensive logging and monitoring for identity-centric attack indicators. Deploy the following detection rules with high-priority alerting:
Okta/Entra ID Detection Queries:
// Microsoft Sentinel: MFA Device Enrollment Following Password Reset
SecurityEvent
| where TimeGenerated > ago(30m)
| where EventID == 4724 // Password reset event
| join kind=inner (
AuditLogs
| where OperationName == "User registered security info"
| where TimeGenerated > ago(30m)
) on UserPrincipalName
| where (AuditLogs.TimeGenerated - SecurityEvent.TimeGenerated) < 30m
| project UserPrincipalName, PasswordResetTime=SecurityEvent.TimeGenerated,
MFAEnrollmentTime=AuditLogs.TimeGenerated, SourceIP=AuditLogs.IPAddress
| extend RiskScore = "CRITICAL"
Google Workspace Detection Queries:
# Google Workspace Takeout Export Detection (>500MB threshold)
# Query via Google Workspace Admin SDK Reports API
{
"eventName": "takeout_export_archive_created",
"parameters": [
{
"name": "archive_size_bytes",
"intValue": ">= 524288000" # 500MB threshold
}
]
}
# Alert on: Any Takeout export >500MB OR any export initiated outside business hours
Salesforce Data Loader Detection:
-- Salesforce Setup Audit Trail: Bulk API Usage Detection
SELECT CreatedDate, CreatedById, Action, Section
FROM SetupAuditTrail
WHERE Action LIKE '%Bulk%' OR Action LIKE '%Export%'
AND CreatedDate > LAST_N_DAYS:7
ORDER BY CreatedDate DESC
-- Alert on: Bulk API calls outside business hours OR >10,000 records exported in single session
PowerShell User-Agent Detection (SharePoint/OneDrive):
// Microsoft Sentinel: PowerShell-based File Downloads
OfficeActivity
| where Operation == "FileDownloaded" or Operation == "FileAccessed"
| where UserAgent contains "PowerShell"
| summarize FileCount=count(), TotalBytes=sum(Size) by UserPrincipalName, UserAgent, ClientIP
| where FileCount >= 20 or TotalBytes >= 524288000 // 20 files OR 500MB
| extend RiskScore = "HIGH"
Security Notification Email Deletion:
// Gmail API: Deletion of Security Alerts
{
"userId": "me",
"query": "subject:(Security method enrolled OR New sign-in OR MFA verification) is:deleted"
}
// Alert threshold: >=2 security notification deletions within 30 minutes
High-Fidelity Behavioral Indicators:
- Multiple MFA enrollments from single source IP (indicates compromised help desk operator or automated attack)
- Admin actions from VPN/TOR infrastructure (policy changes, session terminations, MFA policy updates)
- After-hours access patterns (2 AM - 4 AM local time) combined with bulk export operations
- Simultaneous access from impossible geographic locations (geofencing violations)
- OAuth app authorization for applications not on enterprise whitelist
👥 User Awareness & Help Desk Hardening
Immediate Help Desk Protocol Changes:
- Mandatory live video verification: All account modification requests (password reset, MFA enrollment, privilege changes) require live video call where user holds government-issued photo ID next to their face for visual comparison against employee corporate record
- Out-of-band manager approval: Require manager confirmation via separate communication channel (Signal, encrypted SMS, phone call to known-good number) before processing any account changes
- Callback verification: Never process requests from inbound cold calls; always call user back at phone number listed in corporate directory
- Third-party vendor verification: For requests claiming to originate from third-party vendors, independently contact vendor using trusted contact information from procurement records, not contact details provided by caller
- Reject PII-only verification: Do not accept employee ID, SSN, manager name, or project details as sole identity verification; all of these data points are compromised in previous breaches
Employee Security Awareness Training:
- Distribute threat bulletin describing ShinyHunters vishing methodology with real-world examples
- Educate employees on warning signs: off-hours calls, urgent language, requests to visit unfamiliar login pages, pressure to bypass verification procedures
- Establish clear reporting channel for suspicious calls (dedicated Slack channel, security hotline, incident response email)
- Conduct tabletop exercises simulating vishing attacks to test employee response
📧 Network Security & Access Controls
Identity Provider Hardening:
- Okta ThreatInsight: Enable Okta's threat detection service to automatically block malicious IP addresses and suspicious authentication patterns
- Conditional Access Policies (Entra ID): Configure risk-based conditional access requiring re-authentication for high-risk sign-ins (unusual location, TOR exit nodes, VPN networks)
- Context-Aware Access (Google Workspace): Restrict access to Admin Console, Drive, and Gmail based on device compliance, IP address allow-lists, and geographic boundaries
- Device Compliance Requirements: Block access from unmanaged personal devices; require corporate-managed endpoints with endpoint detection and response (EDR) agents
- Geographic Access Restrictions: For high-risk roles (administrators, finance, HR), restrict access to known geographic regions; alert on authentication attempts from unexpected countries
SaaS Platform Security Controls:
- Salesforce: Enable Event Monitoring to log login history, API calls, report exports, and connected app activity; configure IP allow-lists for administrative access
- Google Workspace: Enforce 2-Step Verification (2SV) for all users; use Advanced Protection Program for high-risk accounts (executives, HR, finance)
- Microsoft 365: Configure Defender for Cloud Apps to monitor OAuth app permissions; automatically revoke high-risk app authorizations
- Atlassian: Enable IP allow-listing for admin areas; configure SAML SSO with session timeout; audit API token creation events
Indicators of Compromise (IoCs)
Network Indicators:
Credential Harvesting Domains (Brand Lookalikes):
- yourcompany-okta[.]com
- mycompany-sso[.]com
- login-entra-id[.]com
- workspace-google-verify[.]com
- salesforce-security-update[.]com
(Note: Actual domains vary per victim; pattern uses legitimate brand + authentication keywords)
TOR Exit Nodes (Known ShinyHunters Infrastructure):
- 185.220.101.XX/24 (AS:tor-project)
- 185.220.102.XX/24 (AS:tor-project)
VPN Infrastructure:
- Mullvad VPN exit nodes (AS:mullvad)
- ProtonVPN exit nodes (AS:protonvpn)
Behavioral IoCs:
Timeline Patterns:
- Password reset at 03:15 AM
- MFA device enrollment at 03:22 AM (7 minutes after reset)
- First SSO authentication at 03:25 AM
- Google Takeout initiated at 03:47 AM
- Security notification emails deleted at 03:52 AM
- Session terminated at 05:30 AM (before business hours begin)
User-Agent Strings:
- PowerShell/7.X.X (used for SharePoint/OneDrive bulk downloads)
- Google-API-Java-Client/1.X.X (used for Google Takeout automation)
- python-requests/2.X.X (API-based data exfiltration)
File Path Indicators (If Malware Deployed):
Credential Harvesting Infrastructure:
- /var/www/html/phishing/okta-clone/index.php
- /opt/vishing/scripts/mfa-bypass-automation.py
- C:\Users\[username]\AppData\Local\Temp\salesforce_export.csv
MITRE ATT&CK Mapping
| Tactic | Technique | ID | Description |
|---|---|---|---|
| Initial Access | Phishing for Information | T1598 | Voice phishing (vishing) calls to gather credentials and PII |
| Initial Access | Valid Accounts: Cloud Accounts | T1078.004 | Use of harvested SSO credentials for legitimate authentication |
| Credential Access | Multi-Factor Authentication Request Generation | T1621 | Social engineering help desk to enroll attacker-controlled MFA device |
| Credential Access | Steal Application Access Token | T1528 | OAuth token theft via authorized malicious applications |
| Defense Evasion | Indicator Removal: Clear Mailbox Data | T1070.008 | Deletion of security notification emails to evade detection |
| Defense Evasion | Use Alternate Authentication Material | T1550 | Exploitation of OAuth tokens and session cookies |
| Collection | Data from Cloud Storage | T1530 | Bulk export via Google Takeout, SharePoint downloads |
| Collection | Email Collection | T1114 | Gmail archive exfiltration, mailbox delegation abuse |
| Exfiltration | Transfer Data to Cloud Account | T1537 | Use of legitimate cloud export tools for data theft |
| Impact | Data Encrypted for Impact | T1486 | Extortion threats involving data encryption or publication |
Bottom Line
ShinyHunters has weaponized the human element of enterprise identity management, demonstrating that sophisticated social engineering defeats traditional technical security controls. The group's January 2026 resurgence as a voice phishing and SaaS extortion syndicate—with confirmed Scattered Spider coordination—represents an existential threat to organizations dependent on cloud identity platforms.
Key Takeaways
✅ Identity is the new attack surface - ShinyHunters' targeting of SSO platforms (Okta, Entra ID, Google Workspace) provides one-to-many access to all downstream SaaS applications, making identity compromise equivalent to full network breach in cloud-first environments.
✅ Traditional MFA is insufficient - Push-notification, SMS, and email-based MFA remain vulnerable to social engineering. Organizations must transition to phishing-resistant MFA (FIDO2 security keys, passkeys) to eliminate human-exploitable authentication workflows.
✅ Help desk is a critical vulnerability - Attackers systematically exploit help desk identity verification procedures by using PII from previous breaches. Organizations must implement live video verification, out-of-band approval, and callback protocols immediately.
✅ The franchise model ensures persistence - ShinyHunters operates as a decentralized brand enabling operational continuity despite law enforcement disruption. Arrests of individual members do not dismantle the collective.
✅ Comprehensive logging is non-negotiable - Without visibility into MFA lifecycle events, OAuth authorizations, bulk exports, and after-hours access patterns, organizations cannot detect ShinyHunters' methodology until extortion demands arrive.
✅ Extortion economics drive evolution - ShinyHunters' shift from data sales ($5K per breach) to extortion ($8M demands) demonstrates financially motivated threat actors continuously optimize toward maximum revenue extraction, making this threat landscape dynamic and escalating.
For Your Clients and Users
Implement emergency session revocation and MFA enrollment lockdown immediately. The cost of transitioning to phishing-resistant authentication and hardening help desk procedures is negligible compared to the regulatory fines, reputational damage, and operational disruption of a ShinyHunters extortion campaign. Treat MFA device enrollment with the same security rigor you would apply to granting domain administrator privileges—because in cloud environments, they are functionally equivalent.
Organizations cannot patch their way out of this threat. Defense requires comprehensive identity hardening, elimination of human-exploitable workflows in credential management, and recognition that the help desk is now a tier-one attack vector requiring the same security controls as internet-facing applications.
ShinyHunters: Security FAQ
1. What is ShinyHunters?
Financially motivated cybercrime collective (since May 2020) evolved from dark web data broker to voice phishing & SaaS extortion syndicate. Compromised 1B+ user records (Tokopedia 91M, Microsoft 500GB, Wattpad 270M, AT&T 110M, Ticketmaster 560M). Operates as decentralized franchise model—four member arrests (June 2024) didn't dismantle operations.
Evolution: Database theft (2020-2021) → Extortion pivot (2021-2024) → Sabbatical (2024-2025) → Voice phishing resurgence (2025-present)
Why It Matters: Extortion is 50-100x more profitable than data sales; voice phishing costs <$100 vs. $50K-300K for zero-days.
2. How does ShinyHunters bypass MFA?
Attack Chain (5 stages):
- Reconnaissance: Attacker obtains stolen PII (employee ID, SSN, manager name) from past breaches
- Vishing Call: Impersonate IT; direct victim to fake credential harvesting site (yourcompany-okta.com)
- Help Desk Social Engineering: Call help desk as victim; use stolen PII to pass verification; request MFA device enrollment
- Help desk enrolls attacker's device as legitimate MFA
- Full Compromise: Attacker authenticates with captured credentials + enrolled MFA device = full access to SSO & all SaaS apps
Secondary Methods:
- MFA Fatigue: 100+ login attempts → user approves one to "make it stop"
- AiTM Phishing: Live interception panel; victim reads MFA code aloud while attacker submits it
Why MFA Fails: Protects against credential phishing, NOT against help desk social engineering. Traditional MFA (SMS, push, email) relies on codes that can be intercepted/stolen.
3. What industries are ShinyHunters targeting in 2026?
Primary Targets:
- Airlines: Vietnam Airlines (3-year dwell), Qantas, Aeroméxico (39M records) → high PII value + regulatory exposure
- Tech/SaaS: Google, Cisco, Workday, Atlassian → customer data access + ability to pay ransom
- Financial Services: Banks, insurance, investment firms → regulatory fines + immediate ransom capability
- Healthcare: Patient PII + clinical data → highest HIPAA fines ($100+ per record)
- Government/Critical Infrastructure: Slow patch cycles + regulatory requirements = pressure to pay
Attack Pattern: Compromise employee Okta/Entra ID → access Salesforce → steal OAuth tokens → bulk export data → extortion demand ($5M-$10M+)
4. How can organizations detect ShinyHunters attacks?
🔴 Critical (Respond <1 hour):
- MFA device enrollment within 30 minutes of password reset (same user) → revoke sessions, investigate
- Multiple MFA enrollments from single IP within 10 minutes (3+ users) → help desk compromise likely
- Google Takeout export >500MB → bulk Gmail/Drive/Contacts exfiltration
- PowerShell user-agent in SharePoint/OneDrive downloads (≥20 files in 15 min) → automated bulk download
- Deletion of security notification emails (≥2 in 30 min) → attacker covering tracks
- Admin actions from Tor/Mullvad/residential proxy → compromised admin account
Action: Kill sessions, revoke tokens, reset credentials, preserve logs for forensics.
5. What is the connection between ShinyHunters and Scattered Spider?
FBI Confirmation (September 2025): Formal link between Scattered Spider (UNC6395) & ShinyHunters (UNC6040/UNC6240) in coordinated Salesforce campaigns.
Evidence: Identical TTPs, simultaneous sector targeting (airlines June-July 2025), shared VPN/proxy infrastructure.
Division of Labor:
- Scattered Spider provides: Vishing expertise, help desk bypasses, "Access-as-a-Service"
- ShinyHunters provides: Data exfiltration, dark web monetization, extortion infrastructure, Trinity of Chaos leak site
Impact: Consolidation of cybercrime ecosystem—complementary skills = formidable threat.
6. What is phishing-resistant MFA and why is it critical?
Cryptographic authentication requiring physical possession or biometric verification. Private key never leaves device; authentication cryptographically bound to legitimate domain (okta.company.com ≠ fake-okta.com).
Options:
- FIDO2 Keys (YubiKey, Google Titan): $40-80, USB/NFC, best for admins/executives
- Passkeys (Face ID, Touch ID, Windows Hello): $0, built-in, best for all users
- Smart Cards: $100-300+, high overhead, government standard
Why It Defeats ShinyHunters: No codes to intercept, no help desk bypass possible, domain binding prevents phishing redirects.
CISA Recommendation: "Make transitioning to phishing-resistant MFA a high-priority effort."
7. How should help desk procedures change?
5-Layer Defense Protocol:
-
Callback Verification (Mandatory)
- Never process cold calls
- Look up user's number in corporate directory; call them back
- Cost: 1 minute per request
- Blocks: ~95% of vishing calls
-
Live Video ID (For MFA/Admin Changes)
- User holds government photo ID next to face on video call
- Help desk visually confirms match
- Cost: 3 minutes per request
-
Manager Approval (Out-of-Band)
- Manager confirms via separate channel (phone, not email)
- "Yes, employee requested this change today"
- Cost: 2 minutes per request
-
Managed Device Only (Technical)
- Only company-managed/Intune-enrolled devices can enroll MFA
- Blocks attacker's personal smartphone
-
Help Desk Monitoring (Continuous)
- Alert on unusual password reset volume per agent
- Alert on resets for high-privilege accounts
- Quarterly spot-check: call 5-10 users to verify they requested resets
- Cost: 10 hours per quarter per 50 agents
Immediate: Implement callback verification + video ID for MFA changes 30 Days: Transition from cold calls to self-service portal 90 Days: Implement risk-based conditional access policies