Lotus Panda Chrysalis: Notepad++ Supply Chain Attack | 2026

Executive Summary
Since June 2025, the Chinese state-sponsored threat actor Lotus Panda (also known as Lotus Blossom, Billbug, Spring Dragon) conducted a sophisticated supply chain attack compromising the infrastructure hosting Notepad++, a text editor used by 300,000+ organizations worldwide. By exploiting insufficient update verification controls, attackers selectively redirected update requests from high-value targets to attacker-controlled servers, delivering a previously undocumented custom backdoor dubbed Chrysalis.inva
The campaign represents a critical evolution in Lotus Panda's operational capabilities: from deploying Sagerunex remote access trojans (RATs) to operating custom, feature-rich implants with advanced evasion techniques. The attack targeted government organizations (Philippines), financial institutions (El Salvador), telecommunications providers (Vietnam), and IT service providers across Southeast Asia and Central America—consistent with Lotus Panda's historical focus on cyber-espionage and strategic intelligence collection.
Critical Finding: Lotus Panda maintained persistent access to Notepad++'s infrastructure for 6 months following the hosting provider's initial remediation (September 2, 2025 → December 2, 2025), demonstrating state-sponsored sophistication in credential-based persistence and long-term operational planning. Only ~12 machines were directly compromised through surgical IP-based targeting, making this attack invisible to most users and researchers.
The Threat Actor: Lotus Panda Profile & Evolution
Lotus Panda is a Chinese state-sponsored advanced persistent threat (APT) group active since at least 2009, with formal identification by Palo Alto Networks Unit 42 in June 2015. The group's operational focus centers on cyber-espionage and strategic intelligence collection targeting Southeast Asia and Central America.
Historical Timeline & Capability Evolution
| Period | Operational Focus | Primary Tools | Geographic Targets |
|---|---|---|---|
| 2009–2015 | Early reconnaissance operations | Undocumented RATs | Southeast Asia (Philippines, Vietnam, Hong Kong, Taiwan) |
| 2015–2022 | Sagerunex RAT dominance | Sagerunex backdoor variants (Dropbox, Twitter, Zimbra C2) | Government agencies, defense contractors, certificate authorities |
| 2022–2025 | Advanced tradecraft development | DLL sideloading (Bitdefender, Trend Micro abuse), service persistence | Asia + Central America expansion (El Salvador) |
| 2025 | Chrysalis era & supply chain sophistication | Chrysalis backdoor, Microsoft Warbird obfuscation, selective targeting | Multi-region government/financial/telecom sectors |
Known Aliases
- Lotus Panda (primary identifier)
- Lotus Blossom (alternative primary)
- Billbug (acronym-based)
- Bronze Elgin (Microsoft designation)
- Spring Dragon
- Thrip
- Raspberry Typhoon
Attribution Confidence: Medium (Rapid7)
Evidence Basis:
✅ Identical Tradecraft: DLL sideloading abuse of renamed Bitdefender Submission Wizard directly mirrors Symantec's documented Lotus Panda attacks (April 2025)
✅ Cryptographic Confirmation: Same public key extracted from Cobalt Strike beacons across multiple Chrysalis loader samples suggests unified command infrastructure
✅ Targeting Patterns: Selective attacks on government, telecommunications, and financial sectors in Philippines, Vietnam, El Salvador—exact match to Lotus Panda's historical area of responsibility (AOR)
✅ Capability Progression: Documented evolution from Sagerunex (2016-2025) → Chrysalis (2025) suggests unified threat actor with sophisticated development capability
✅ Operational Sophistication: Monthly infrastructure rotation, victim-specific payload customization, 6-month persistence after initial remediation—consistent with state-sponsored actor planning
The Supply Chain Attack: How Notepad++ Was Weaponized
Attack Vector & Initial Compromise
On an undisclosed date in June 2025, Lotus Panda compromised the shared hosting infrastructure serving Notepad++ update requests. The root cause was weak segregation of shared hosting environments, allowing attackers to:
- Intercept update traffic destined for Notepad++ users
- Redirect traffic to attacker-controlled infrastructure
- Modify HTTP requests in-flight without cryptographic detection
Exploitation of Vulnerability: Notepad++ versions <8.8.9 lacked cryptographic signature verification of update packages. The legitimate updater (GUP.exe) blindly executed whatever binary was served by the hosting provider, creating a perfect supply chain attack vector.
Selective Targeting Mechanism: Surgical Precision
Unlike indiscriminate supply chain attacks (SolarWinds, 3CX), Lotus Panda employed surgical precision targeting:
Targeting Method:
- IP-based filtering: Attacker-controlled infrastructure filtered incoming update requests by source IP address
- Selective redirection: Only users from specific IP ranges (East Asian telecommunications, financial sectors) were redirected to malicious servers
- Legitimate updates for others: All other users received legitimate updates, maintaining operational cover
Result: The attack remained invisible to most users, researchers, and security vendors—only ~12 machines across 4 countries were directly compromised.
Targeted Regions & Sectors
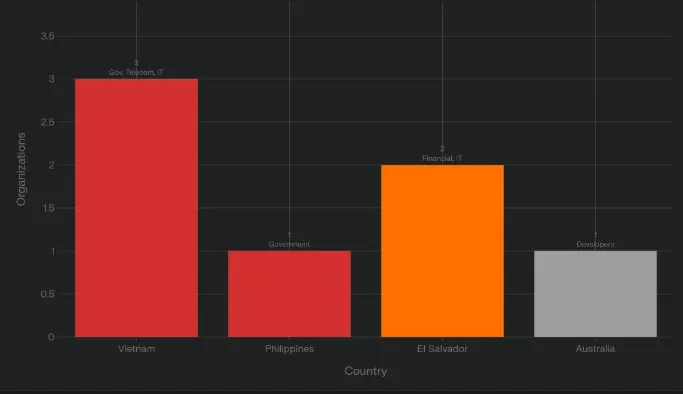
Timeline: From Zero-Day to 6-Month Persistence
| Date | Event | Status |
|---|---|---|
| June 2025 | Lotus Panda compromises Notepad++ hosting provider infrastructure | ⚠️ Initial compromise |
| Late July 2025 | Chain #1 deployment begins (45.76.155.202) - Metasploit downloader variant | 🔴 Active exploitation |
| Mid-September 2025 | Chain #2 deployment (45.76.155.202) - Lua script + optimized payload (140 KB) | 🔴 Active exploitation |
| September 2, 2025 | Hosting provider rotates credentials and loses attacker access | ✅ Partial remediation |
| September 2–December 2, 2025 | Lotus Panda maintains access via stolen administrative credentials | 🔴 Persistent access |
| Early October 2025 | Chain #3 deployment (45.32.144.255) - Direct Chrysalis implant, no reconnaissance | 🔴 Active exploitation |
| Late October 2025 | Multi-URL diversification (95.179.213.0) - Three simultaneous distribution URLs | 🔴 Active exploitation |
| December 2, 2025 | Hosting provider terminates all attacker access | ✅ Full remediation |
| Late September 2025 | First public detection via VirusTotal (Taiwan user) | 🔍 Public disclosure |
| February 2026 | Rapid7 publishes detailed Chrysalis technical analysis | 📢 Public disclosure |
Key Insight: Despite hosting provider remediation on September 2, 2025, Lotus Panda extracted administrative credentials during the initial compromise, enabling 3 months of continued persistence—demonstrating state-sponsored sophistication in long-term operational planning.
The Chrysalis Backdoor: Technical Deep-Dive
Deployment Architecture
Notepad++ User Initiates Update (Help → Check for Updates)
↓
GUP.exe (Legitimate Notepad++ Updater) Executes
↓
DNS/Traffic Interception (Attacker-Controlled Infrastructure)
↓
Redirect to Malicious Update Server
├── 45.76.155.202 (July-September 2025)
├── 45.32.144.255 (October 2025)
└── 95.179.213.0 (Late October 2025)
↓
NSIS Installer Download (update.exe, ~1-140 KB)
↓
GUP.exe Executes Malicious update.exe (No Signature Verification)
↓
NSIS Installer Extraction to Disk:
├── BluetoothService.exe (renamed Bitdefender Submission Wizard - legitimate binary)
├── log.dll (malicious DLL loader)
└── BluetoothService (encrypted Chrysalis shellcode - no file extension)
↓
Windows DLL Sideloading (T1574.002):
- BluetoothService.exe launches
- Windows searches for log.dll in same directory (DLL search order hijacking)
- Malicious log.dll loads instead of legitimate library
↓
Shellcode Decryption & Execution:
- log.dll decrypts "BluetoothService" file (encrypted shellcode)
- Executes Chrysalis backdoor in memory (fileless execution)
↓
Chrysalis Implant Establishes Persistence:
- Registry Run key: HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- Windows Service installation (name varies per sample)
- Awaits commands from C2 infrastructure
↓
Command & Control Communication:
- Primary C2: api.skycloudcenter[.]com
- Secondary C2: api.wiresguard[.]com
- Exfiltration: temp[.]sh, self-dns.it[.]com, safe-dns.it[.]com, cdncheck.it[.]com
Chrysalis Capabilities
🔍 Information Gathering
- System reconnaissance:
whoami,tasklist,ipconfig,netstat,systeminfo - File enumeration: Directory listing, file metadata extraction
- Network mapping: Active connection enumeration, route discovery
- Process monitoring: Running processes, parent-child relationships
🎯 Remote Code Execution
- Interactive shell spawning: Direct
cmd.exeaccess with arbitrary command execution - Process creation: Launch executables with custom arguments
- File operations: Upload malicious payloads, download sensitive data
- DLL injection: Code injection into running processes for lateral movement
🔑 Persistence Mechanisms
- Registry modification:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run(boot persistence) - Windows Service installation: Service-based persistence with automatic restart
- Automatic startup: Executes on system reboot without user interaction
🛡️ Advanced Evasion Techniques
- Custom string obfuscation: Position-dependent character transforms via bit rotation + conditional XOR + index-based arithmetic
- Multi-layered shellcode loaders: Decoy shellcodes confuse analysis
- Undocumented system calls:
NtQuerySystemInformationfor stealth enumeration - Reflective code loading: Execute code in memory without disk artifacts
- Microsoft Warbird integration: Weaponized undocumented Microsoft code obfuscation framework
Obfuscation Deep-Dive: Position-Dependent String Encryption
Mechanism:
Chrysalis employs a two-stage obfuscation process that encrypts identical characters differently based on their position in the string:
-
Encryption subroutine: Character transformation using:
- Bit rotations (left/right shifts)
- Conditional XOR operations
- Index-based arithmetic (position in string affects transformation)
-
Decryption subroutine: Reverses the process at runtime just before string use
Example:
Original String: "whoami"
Position: 0 1 2 3 4 5
Character 'a' at position 3:
→ Bit rotate left by 3
→ XOR with 0x4A
→ Add position index (3)
→ Result: 0x7C
Character 'a' at different position would produce DIFFERENT encrypted byte
Purpose: Defeat static analysis, signature-based detection, and YARA rules that rely on string patterns.
Microsoft Warbird Weaponization
Microsoft Warbird is an undocumented internal code protection framework used by Microsoft to obfuscate Windows components. In September 2024, Cirosec published a proof-of-concept (PoC) demonstrating how to weaponize Warbird for malware obfuscation.
Lotus Panda's Adaptation:
- Timeline: PoC published September 2024 → Weaponized in Chrysalis by December 2024
- Weaponization speed: ~3 months from public research to operational deployment
- Demonstrates: Rapid adaptation of public security research into state-sponsored operational capability
Three Distinct Infection Chains: Evolution Over Time
Chain #1: Late July – Early August 2025
Distribution URL: http://45.76.155[.]202/update/update.exe
Payload Profile:
- NSIS Installer size: ~1 MB
- Reconnaissance phase: Sent heartbeat with system information (
whoami,tasklist) to attacker - DLL sideloading variant: Abused
ProShow.exe(legitimate presentation software) - Dual shellcodes: Decoy shellcode (does nothing) + Metasploit downloader (actual payload)
Evasion Tactics:
- First shellcode is a distraction that executes harmless code
- Second shellcode contains actual Metasploit downloader
- Confuses automated analysis systems by providing fake payloads
- Eventually retrieves Cobalt Strike Beacon from C2 infrastructure
Detection Timeline:
- Deployed: Late July 2025
- First public detection: Late September 2025 (VirusTotal submission by Taiwan user)
- Detection lag: 2+ months
File Hash: 8e6e505438c21f3d281e1cc257abdbf7223b7f5a (SHA1)
Chain #2: Mid-September – End September 2025
Distribution URL: http://45.76.155[.]202/update/update.exe (same URL, different payload)
Payload Profile:
- NSIS Installer size: ~140 KB (87% size reduction from Chain #1)
- Extended reconnaissance: Added
netstatcommand for network connection enumeration - Lua script execution: New technique for shellcode deployment
- Payload: Metasploit downloader + Cobalt Strike Beacon
Changes from Chain #1:
- Payload size optimization: Reduced disk footprint from 1 MB → 140 KB
- Working directory obfuscation:
%APPDATA%\Adobe\Scripts(masquerading as Adobe) - Additional reconnaissance: Network connections, active listeners
- Different C2 URLs:
self-dns.it[.]com,safe-dns.it[.]com
Late September Variant:
- Added:
systeminfocommand (comprehensive system enumeration) - C2 infrastructure change: Switched to
cdncheck.it[.]com - Indicates: Monthly C2 infrastructure rotation strategy
File Hashes:
- Mid-September:
573549869e84544e3ef253bdba79851dcde4963a(SHA1) - Late September:
821c0cafb2aab0f063ef7e313f64313fc81d46cd(SHA1)
Chain #3: Early October 2025
Distribution URL: http://45.32.144[.]255/update/update.exe (NEW IP ADDRESS)
Payload Profile:
- NSIS Installer
- Removed reconnaissance phase: No system information sending (stealth improvement)
- Direct payload deployment: Immediate implant installation without reconnaissance
- Components:
BluetoothService.exe+log.dll+ encrypted shellcode - Matches: Rapid7's detailed Chrysalis findings
Strategic Shift from Chain #2:
- Elimination of reconnaissance phase = fewer detection opportunities
- Assumes: Attacker has already profiled target through previous chains
- Direct implant deployment for maximum operational speed
- Suggests: High-confidence targeting of known high-value victims
File Hash: d7ffd7b588880cf61b603346a3557e7cce648c93 (SHA1)
Late October 2025: Multi-URL Diversification
Distribution URLs (simultaneous use):
http://95.179.213[.]0/update/update.exehttp://95.179.213[.]0/update/install.exehttp://95.179.213[.]0/update/AutoUpdater.exe
Operational Strategy:
- Filename diversification: Prevents simple file-based blocking rules
- Same attacker IP:
95.179.213.0across all three URLs (infrastructure consolidation) - Hybrid techniques: Combination of Chain #2 + Chain #3 capabilities
- Demonstrates: Sophistication in operational security and evasion
Infrastructure Rotation Pattern:
| Period | IP Address | Monthly Change |
|---|---|---|
| July-August 2025 | 45.76.155.202 | Initial infrastructure |
| September 2025 | 45.76.155.202 | Static (same IP) |
| Early October 2025 | 45.32.144.255 | ✅ IP rotation |
| Late October 2025 | 95.179.213.0 | ✅ IP rotation |
Purpose: Monthly IP changes prevent pattern detection and simple IP-based blocking at network perimeter.
Why This Matters: The Developer-as-Target Paradigm
The Strategic Value of Developer Machines
Developers are now critical intelligence collection targets for state-sponsored actors. Developer workstations provide direct access to:
- Source code repositories: Intellectual property, proprietary algorithms, trade secrets
- Infrastructure credentials: Cloud access keys, database passwords, API tokens
- Customer data: Production database access, customer lists, financial records
- Strategic information: Product roadmaps, M&A plans, business intelligence
Key Challenges Enabling This Attack
1. Insufficient Update Verification
- Problem: Notepad++ versions <8.8.9 had no cryptographic signature verification
- Impact:
GUP.exeblindly executed any binary served by the hosting provider - Solution: Cryptographic signatures with certificate pinning
2. Shared Hosting Vulnerabilities
- Problem: Weak segregation allowed attacker to intercept traffic for other tenants
- Impact: Single hosting compromise affected millions of potential targets
- Solution: Dedicated hosting infrastructure for critical software distribution
3. Delayed Credential Rotation
- Problem: Hosting provider failed to rotate all administrative credentials after initial remediation
- Impact: Attacker maintained access for 3 additional months (September-December 2025)
- Solution: Comprehensive credential rotation procedures post-compromise
Defensive Posture: Immediate Actions
🔴 Patch Immediately (Critical Priority)
Action: Update Notepad++ to version 8.8.9 or later immediately.
Verification:
# Check Notepad++ version
Get-ItemProperty "C:\Program Files\Notepad++\notepad++.exe" | Select-Object VersionInfo
# Compare against vulnerable versions (<8.8.9)
Patch Timeline:
- Vulnerable: Notepad++ versions <8.8.9
- Patched: Notepad++ 8.8.9+ (released December 2025)
- Fix: Cryptographic signature verification of update packages
🔍 Threat Hunting & Detection
File-Based Indicators
Search for malicious files dropped by NSIS installers:
# Search for renamed Bitdefender Submission Wizard (common DLL sideloading target)
Get-ChildItem -Path C:\ -Recurse -ErrorAction SilentlyContinue -Filter "BluetoothService.exe" |
Select-Object FullName, CreationTime, LastWriteTime
# Search for suspicious log.dll (malicious loader)
Get-ChildItem -Path C:\ -Recurse -ErrorAction SilentlyContinue -Filter "log.dll" |
Where-Object { $_.Directory.Name -notmatch "Windows|Program Files" } |
Select-Object FullName, CreationTime, LastWriteTime
# Search for NSIS temporary directories
Get-ChildItem -Path $env:LOCALAPPDATA\Temp -Recurse -ErrorAction SilentlyContinue -Filter "ns*.tmp" |
Select-Object FullName, CreationTime
Process Execution Chain Detection
Microsoft Sentinel (KQL):
// Detect GUP.exe spawning update.exe
DeviceProcessEvents
| where FileName =~ "GUP.exe"
| where ProcessCommandLine contains "update.exe"
| join kind=inner (
DeviceProcessEvents
| where FileName =~ "update.exe"
) on DeviceId
| project Timestamp, DeviceName, AccountName, FileName, ProcessCommandLine, InitiatingProcessFileName
| order by Timestamp desc
Splunk (SPL):
index=windows sourcetype=WinEventLog:Security EventCode=4688
| search (process_name="GUP.exe" OR process_name="update.exe" OR process_name="BluetoothService.exe")
| transaction host maxspan=5m
| search process_name="GUP.exe" AND process_name="update.exe"
| table _time, host, user, process_name, process_command_line, parent_process_name
| sort -_time
Network-Based Detection
Search for C2 communication:
index=proxy OR index=firewall
| search (dest="api.skycloudcenter.com" OR dest="api.wiresguard.com" OR dest="self-dns.it.com" OR dest="safe-dns.it.com" OR dest="cdncheck.it.com" OR dest="temp.sh")
| stats count by src_ip, dest, dest_port, action
| where count > 5
DNS query monitoring:
DnsEvents
| where Name contains "skycloudcenter" or Name contains "wiresguard" or Name contains "self-dns.it" or Name contains "safe-dns.it" or Name contains "cdncheck.it"
| project TimeGenerated, Computer, ClientIP, Name, QueryType
| order by TimeGenerated desc
Registry Persistence Detection
# Check for suspicious Run key entries
Get-ItemProperty -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Run" |
Select-Object PSChildName, * -ExcludeProperty PS* |
Where-Object { $_.PSChildName -match "Bluetooth|Adobe|log" }
# Enumerate services with suspicious names
Get-Service | Where-Object { $_.Name -match "Bluetooth" -and $_.Status -eq "Running" } |
Select-Object Name, DisplayName, StartType, Status |
ForEach-Object {
$servicePath = (Get-WmiObject Win32_Service -Filter "Name='$($_.Name)'").PathName
[PSCustomObject]@{
ServiceName = $_.Name
DisplayName = $_.DisplayName
Path = $servicePath
Status = $_.Status
}
}
👥 User Awareness & Training
- Developer security training: Educate developers on supply chain attack risks
- Update verification: Train users to verify software signatures before installation
- Suspicious behavior reporting: Encourage reporting of unusual update prompts or unexpected system behavior
- Least privilege principle: Run development tools with minimal required permissions
📧 Email & Network Security
Email Security
- Block attachment types: Block
.nsi,.exefrom unknown senders - Sandbox execution: Detonate all executables in isolated environments before delivery
- URL filtering: Block known malicious domains in email gateway
Network Security
- DNS sinkholing: Redirect known C2 domains to sinkhole servers
- Egress filtering: Block outbound connections to high-risk ASNs
- TLS inspection: Inspect encrypted traffic for known C2 patterns
Blocklist for firewall/DNS:
api.skycloudcenter.com
api.wiresguard.com
self-dns.it.com
safe-dns.it.com
cdncheck.it.com
temp.sh
45.76.155.202
45.32.144.255
95.179.213.0
Indicators of Compromise (IoCs)
File Hashes (SHA1)
Chain #1 (July-August 2025):
8e6e505438c21f3d281e1cc257abdbf7223b7f5a (update.exe)
90e677d7ff5844407b9c073e3b7e896e078e11cd (update.exe variant)
Chain #2 (September 2025):
573549869e84544e3ef253bdba79851dcde4963a (update.exe)
13179c8f19fbf3d8473d49983a199e6cb4f318f0 (update.exe variant)
821c0cafb2aab0f063ef7e313f64313fc81d46cd (October variant)
Chain #3 (October 2025):
d7ffd7b588880cf61b603346a3557e7cce648c93 (update.exe)
Network Indicators
C2 Infrastructure:
api.skycloudcenter[.]com
api.wiresguard[.]com
61.4.102.97
59.110.7.32
124.222.137.114
Update Distribution Servers:
45.76.155.202 (July-September 2025)
45.32.144.255 (October 2025)
95.179.213.0 (Late October 2025)
Exfiltration Domains:
temp[.]sh
self-dns.it[.]com
safe-dns.it[.]com
cdncheck.it[.]com
File Paths
Typical Installation Locations:
%LOCALAPPDATA%\Temp\ns*.tmp\ (NSIS temporary extraction)
%APPDATA%\Adobe\Scripts\ (Chain #2 working directory)
C:\Users\[username]\BluetoothService.exe
C:\Users\[username]\log.dll
C:\Users\[username]\BluetoothService (encrypted shellcode, no extension)
Registry Keys
Persistence Mechanisms:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
HKLM\SYSTEM\CurrentControlSet\Services\[ServiceName] (varies per sample)
Behavioral Indicators
Shell Commands Executed by Chrysalis:
whoami
tasklist
ipconfig
netstat
systeminfo
cmd.exe /c [arbitrary commands]
Process Execution Patterns:
GUP.exe → update.exe → BluetoothService.exe → log.dll → shellcode execution
MITRE ATT&CK Mapping
| Tactic | Technique | ID | Description |
|---|---|---|---|
| Initial Access | Supply Chain Compromise | T1195.002 | Compromise of software supply chain (Notepad++ hosting infrastructure) |
| Execution | User Execution | T1204.002 | Malicious file execution via legitimate update mechanism (GUP.exe) |
| Persistence | Boot or Logon Autostart Execution | T1547.001 | Registry Run Keys/Startup Folder modification |
| Persistence | Create or Modify System Process | T1543.003 | Windows Service installation for automatic startup |
| Defense Evasion | Masquerading | T1036.005 | Match Legitimate Name or Location (renamed Bitdefender binary) |
| Defense Evasion | Hijack Execution Flow | T1574.002 | DLL Side-Loading via renamed legitimate executables |
| Defense Evasion | Obfuscated Files or Information | T1027.010 | Command Obfuscation (position-dependent string encryption) |
| Defense Evasion | Deobfuscate/Decode Files or Information | T1140 | Runtime decryption of encrypted shellcode |
| Discovery | File and Directory Discovery | T1083 | Enumeration of files and directories for intelligence gathering |
| Discovery | System Information Discovery | T1082 | Execution of systeminfo, whoami, ipconfig commands |
| Discovery | System Network Connections Discovery | T1049 | Execution of netstat for active connection enumeration |
| Discovery | Process Discovery | T1057 | Execution of tasklist for running process enumeration |
| Collection | Data from Local System | T1005 | Collection of system information and files for exfiltration |
| Command and Control | Application Layer Protocol | T1071.001 | Web Protocols (HTTP/HTTPS) for C2 communication |
| Command and Control | Web Service | T1102 | Use of web services for C2 (temp.sh for exfiltration) |
| Exfiltration | Exfiltration Over C2 Channel | T1041 | Data exfiltration over established C2 infrastructure |
Bottom Line
Lotus Panda's compromise of Notepad++ represents a permanent paradigm shift in state-sponsored supply chain attack sophistication: selective IP-based targeting replaced spray-and-pray attacks, making detection nearly impossible for most users and researchers.
Key Takeaways
✅ Selective Targeting Defeats Mass Detection — By compromising only ~12 machines across 4 countries through IP filtering, Lotus Panda remained undetected for 6 months while targeting high-value government, financial, and telecommunications organizations.
✅ Developer Machines Are Now Strategic Intelligence Targets — Access to source code repositories, infrastructure credentials, and customer data makes developers lucrative targets for state-sponsored cyber-espionage campaigns.
✅ Cryptographic Update Verification Is Non-Negotiable — Notepad++'s lack of signature verification enabled the entire attack chain. All software must implement end-to-end cryptographic verification independent of hosting infrastructure trust.
✅ Post-Compromise Credential Rotation Must Be Comprehensive — Lotus Panda maintained access for 3 months after initial remediation by exploiting incomplete credential rotation—demonstrating that partial remediation is equivalent to no remediation.
✅ Monthly Infrastructure Rotation Defeats Simple Blocking — Attacker IP address rotation every 30 days prevented effective perimeter-based blocking, requiring behavioral detection instead of indicator-based approaches.
For Security Teams and Organizations
Threat hunt immediately if your organization uses Notepad++ and operates in Southeast Asia, Central America, or government/financial/telecommunications sectors. The ~12 compromised machines identified publicly may represent only the tip of the operational iceberg—state-sponsored actors typically maintain multiple undisclosed access vectors.
Patch to Notepad++ 8.8.9+ immediately and implement comprehensive threat hunting using the detection queries provided above. Assume compromise if you cannot definitively prove absence of indicators.
Review ALL software update mechanisms for cryptographic signature verification. If verification relies solely on hosting provider trust, your supply chain is exploitable at scale.
Frequently Asked Questions
What is the Chrysalis backdoor?
Chrysalis is a custom backdoor developed by Chinese APT group Lotus Panda, deployed via a supply chain attack on Notepad++ hosting infrastructure from June-December 2025. It features advanced obfuscation (Microsoft Warbird), DLL sideloading, and remote code execution capabilities targeting government, financial, and telecommunications sectors.
How do I know if my Notepad++ installation was compromised?
Check for: (1) Notepad++ version <8.8.9, (2) files named BluetoothService.exe or log.dll in non-system directories, (3) network connections to api.skycloudcenter.com or api.wiresguard.com, (4) suspicious Registry Run keys. Use the threat hunting queries provided in the "Detection & Response" section above.
Is this attack still active in 2026?
No. The hosting provider terminated all attacker access on December 2, 2025. However, machines compromised during June-December 2025 may still contain dormant Chrysalis implants. Threat hunting is recommended for organizations in affected sectors/regions.
What makes this different from other supply chain attacks?
Unlike SolarWinds or 3CX (mass compromise), Lotus Panda used selective IP-based targeting to compromise only ~12 high-value machines across 4 countries. This surgical precision made detection nearly impossible for most users and security vendors.
How long did Lotus Panda have access to Notepad++ infrastructure?
6 months total: June 2025 (initial compromise) → September 2, 2025 (hosting provider remediation) → December 2, 2025 (final termination via comprehensive credential rotation). The attacker maintained access for 3 months after initial remediation through stolen credentials.
What sectors should be most concerned?
High-priority sectors: Government agencies, telecommunications providers, financial institutions, IT service providers in Vietnam, Philippines, El Salvador, and Australia. Secondary concern for any organization with developers using Notepad++ for handling sensitive code or infrastructure.
REFERENCES
-
Rapid7: The Chrysalis Backdoor - A Deep Dive into Lotus Blossom's Toolkit, February 1, 2026
-
Kaspersky: Notepad++ Supply Chain Attack Breakdown, February 2, 2026
-
TheHackerNews: Notepad++ Hosting Breach Attributed to China-Linked Lotus Blossom, February 2, 2026
-
TechNadu: Notepad++ Hijacking Incident Deploying Backdoor Linked to Lotus Blossom, February 2, 2026
-
The Register: Notepad++ Hijacking Blamed on Chinese Lotus Blossom Crew, February 1, 2026
-
BleepingComputer: Notepad++ Update Feature Hijacked by Chinese State Hackers, February 2, 2026
-
CTRL Magazine: Targeted Supply‑Chain Attacks Abuse Notepad++ Update Infrastructure, February 2, 2026
-
CISO Node: The Chrysalis Backdoor - When Espionage Tooling Evolves in Plain Sight, February 2, 2026
-
TheHackerNews: Chinese APT Lotus Panda Targets Governments with Sagerunex Backdoor, March 2025
-
Picus Security: Lotus Blossom - New Sagerunex Backdoor Variants, March 27, 2025